Create a Deployment
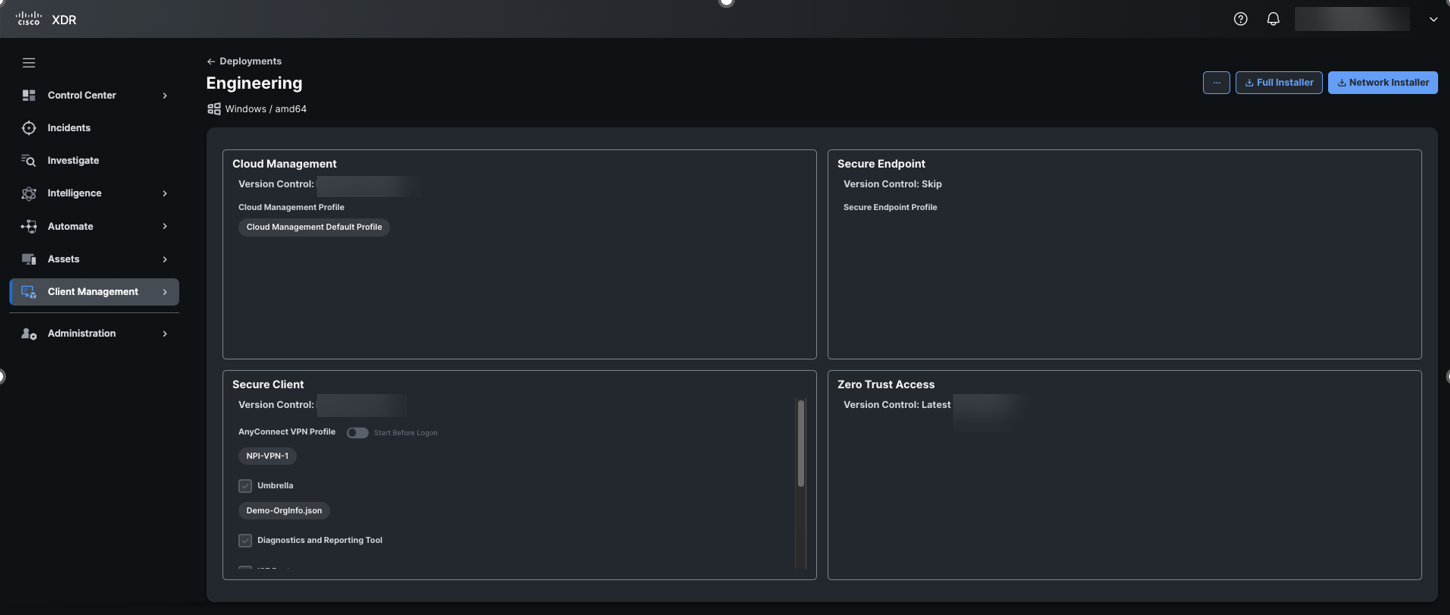
The Deployments page provides a list of all the Cisco Secure Client deployments in your Cisco XDR organization and allows users to define a list of all the packages and related profiles that must be installed on all the computers in a specific deployment within an organization (for example, QA department).
- To create a new deployment, navigate to Client Management > Deployments and click on New. You can also edit existing deployments from the list displayed.
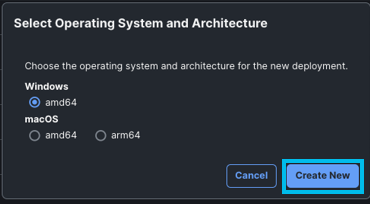
- When prompted, select the operating system for the deployment, that is, either Windows
or macOS.
In this example, Windows is selected.
-
Click Create New.
-
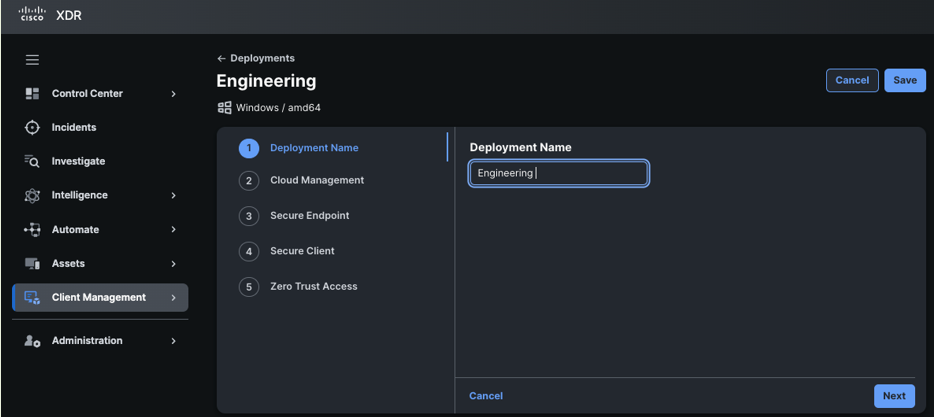
Specify a name for the deployment: This name will be included in the file name of the final package after the deployment configuration is complete.
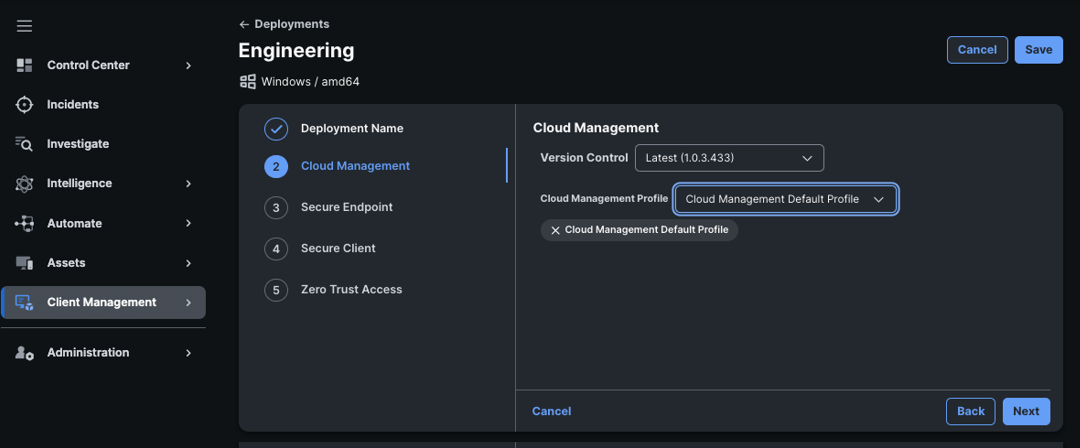
Every deployment includes the Cloud Management module and profile. Choose a version for both the Cloud Management module and the Cloud Management profile. While the default Cloud Management profile typically works well, administrators have the option to create a custom profile, if needed. For example, you might want different check-in intervals or update Windows for certain user groups.
-
From the Version Control drop-down list, choose the Secure Endpoint connector version that you want to deploy. If you prefer to not include the Secure Endpoint module, choose Skip and proceed. In this example, Skip is chosen.
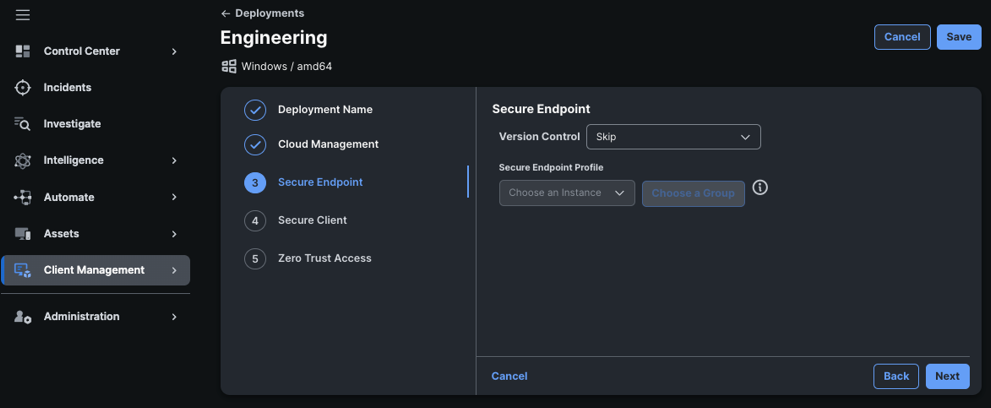
Next, configure the Cisco Secure Client section to include AnyConnect VPN, Umbrella, and DART in the deployment.
If you don't plan to use AnyConnect VPN, you can skip adding a VPN profile. After completing the cloud deployment, push the VPNDisable_ServiceProfile.xm file to the VPN profile directory (as described earlier in Customize Windows Installation of Cisco Secure Client guide). This hides the AnyConnect VPN tile in the GUI.To complete the Cisco Secure Client section of the deployment, we selected an existing VPN profile that was either uploaded or created in Client Management using the profile editor. Along with the VPN profile, we enabled the DART and the Umbrella module, specifying the previously uploaded Umbrella OrgInfo.json profile. This configuration generates a deployment package that includes the specified modules and profiles upon installation.
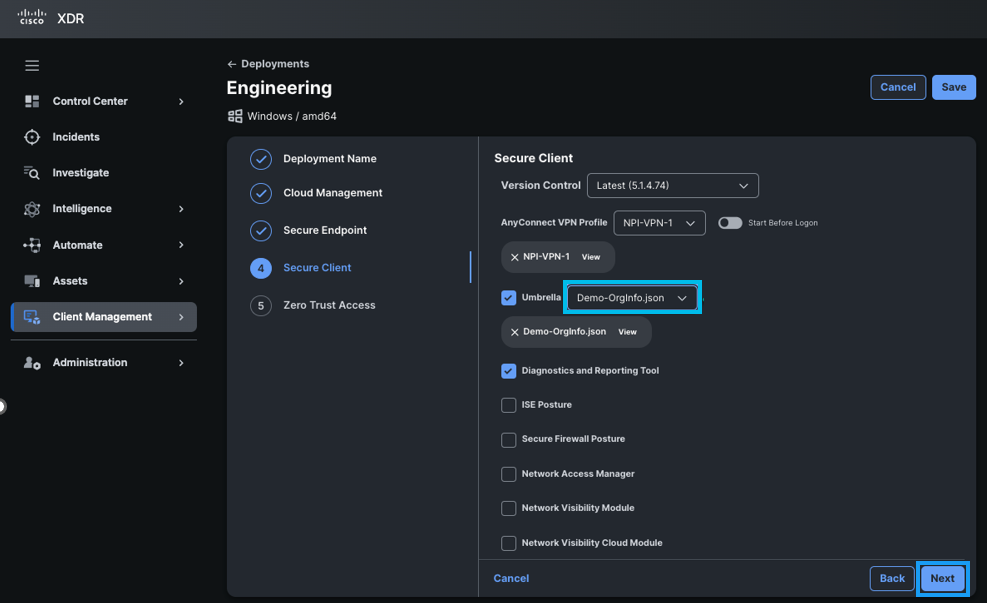
- After completing the deployment configuration, click Next.
For Windows deployments, the administrator will have the option to add the Zero Trust Access (ZTA) module for Cisco Secure Client. While the ZTA module is supported on macOS through other deployment methods, it is not yet supported for cloud deployments using XDR or Cisco Secure Cloud Client Management. The ZTA module is designed to work seamlessly with the Cisco Secure Access solution.
ZTA focuses on knowing, understanding, and controlling who and what is on your network:
- It grants appropriate access based on role or function.
- It controls application access at the network layer.
- By assuming that the network layer is untrustworthy, it helps prevent unauthorized access and breaches.
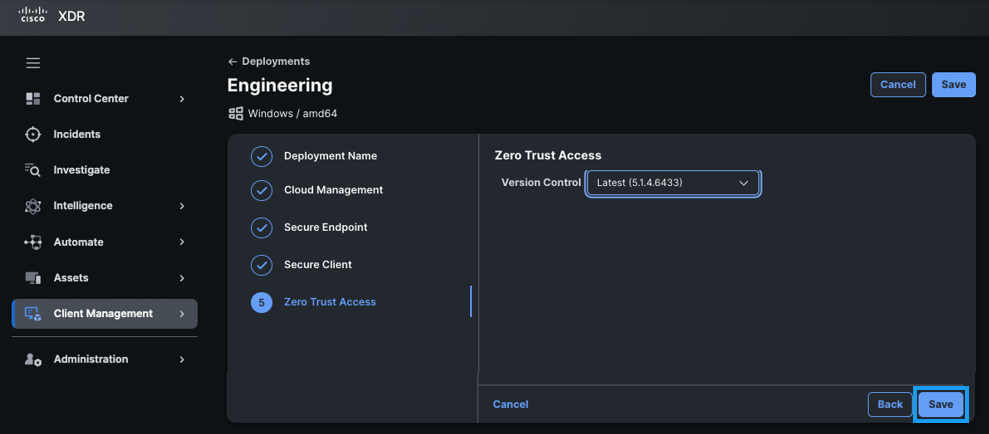
- When you click Save it finalizes the deployment configuration and presents the
Administrator with two installation package options — Network Installer or Full Installer.
- Network Installer: A streamlined installer that includes only the Cloud Management client. When using the Network Installer, it will download the remaining components specified in the deployment in the background.
- Full Installer: A comprehensive package that includes all the installers and profiles configured for the deployment. It is larger than the Network Installer, and when used, it installs the Cloud Management client along with all associated packages from the deployment.
Both the Full and Network installers will link the device to the deployment from which the installer was created. Whenever the device connects to the cloud, it checks the installed packages against the deployment requirements. The device then updates the packages and profiles to match the deployment, but does not downgrade any packages that are newer than those specified in the deployment.