Sources
In a private access rule, add reusable source components. You can also specify sources by entering IP addresses, subnets, and ports, but these are not reusable source components. For more information, see About Configuring Sources in Private Access Rules.
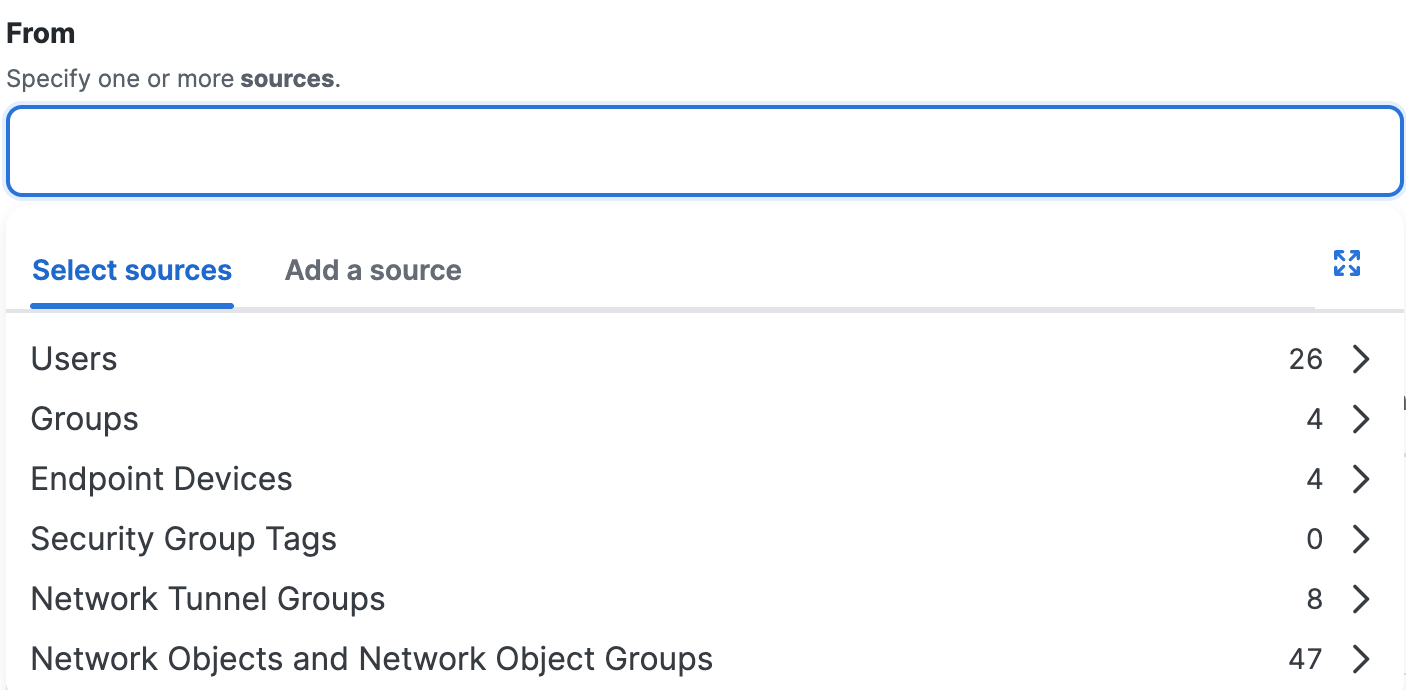
-
You can apply rules to the traffic for the users in the organization.
-
You can apply rules to the traffic for the groups of users in the organization.
-
Security Group Tags
You can apply rules to traffic originating from IP addresses in network segments that include Security Group Tags.
-
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Tunnel Groups.
-
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Objects.
-
You can apply rules to the traffic originating from IP addresses in network segments defined by Network Objects in Network Object Groups.
-
Endpoint Devices
You can apply private access rule security controls to any endpoint device in Secure Access. Endpoint devices in Secure Access include the following:
- Any user device provisioned from an on-premise Active Directory (AD) domain controller (DC) integrated with Secure Access.
- Any user device that has enrolled with Zero Trust Access on the Cisco Secure Client.
-
Be aware that rule-level security features (Configure Security > Intrusion Prevention (IPS) or Configure Security > Security Profile) are not compatible with access rules that have ZTA-enrolled devices as a source (Select Sources > Any Endpoint Device > ZTA Enrolled Devices). Configuring access rules with this combination is not recommended. - Once enrolled or provisioned, user devices are available as sources in private access rules. You can select all endpoint devices in the organization, any AD device, any ZTA enrolled device, ZTA enrolled devices with specific host operating systems (macOS, Windows, iOS, or Android), or individual endpoint devices identified by device name.
For more information about the Cisco Secure Client and enrolling in Zero Trust Access, see Manage Zero Trust Access using Cisco Secure Client on Windows and macOS Devices.
For more information about AD device provisioning, see Manage Users, Groups, and Endpoints Devices.
