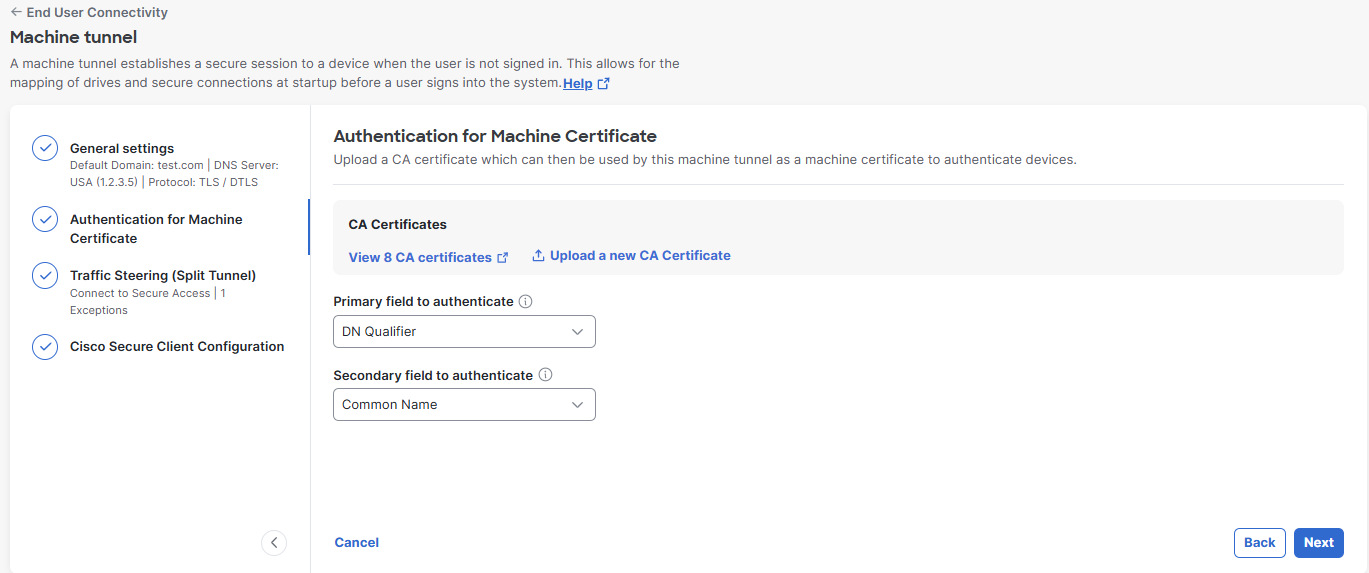
Step 2 – Authentication for Machine Certificate
The machine tunnel is transparent to the end user and disconnects automatically when the user initiates a VPN session. For this tunnel to be created without user interaction, certificate-based authentication is used.
-
Choose CA certificates from the list or click Upload CA certificates. These certificates can be used by the machine tunnel as a machine certificate to authenticate devices. Upload your organization's signed CA root certificate. For more information, see VPN Certificates for User and Device Authentication.
-
Select the certificate-based authentication fields.
- For Primary field to authenticate, choose the certificate field that contains the device name (computer name). Secure Access uses the device name as the machine tunnel identifier. The format of the computer name must match the format of the chosen device identifier. For more information, see Authenticate Device Identity with Active Directory.
- (Optional) For Secondary field to authenticate, choose a secondary attribute to authenticate to Active Directory endpoint devices. You cannot choose the same value for the primary and secondary authentication fields.
Set the Primary field to authenticate option to Common Name, which retrieves the computer name from the CN field in the certificate. The certificate may use the fully-qualified domain name (FQDN) format similar to (computer.domain.tld) or short format (computer) for computer name -
Click Next to configure the Traffic Steering.

