Quarantine File
For SaaS API events on Microsoft OneDrive, SharePoint Online, Box, Dropbox, ServiceNow, or Google Drive, when a file is monitored and a rule violation is detected, you can manually quarantine the file.
- Click the action menu icon (three dots) for any event to view a menu of options. Click
Quarantine file.
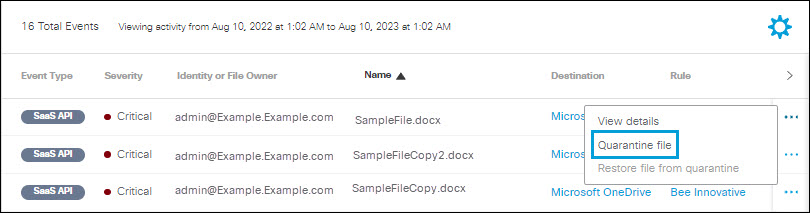
- Click Quarantine.
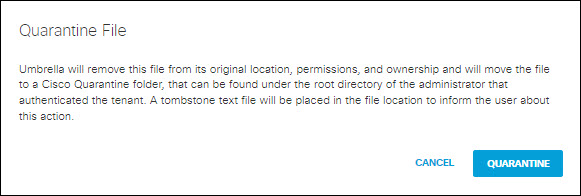
- For Microsoft OneDrive, SharePoint Online, Box, Dropbox, or Google Drive:
- The file identified as exposing sensitive data is moved to the Cisco_Quarantine/DLP folder Secure Access created in the root path of the Global Admin who authorised the tenant.
- The user who authorizes access to Secure Access will have access to the quarantine folder. All other accesses and collaborators are removed. Thus, we recommend that the admin add the relevant DLP Admins as additional collaborators to the folder.
- For ServiceNow:
- The file identified as exposing sensitive data is moved to a table named Cisco_Quarantine_Malware which can be access only by the admin user who authorized the ServiceNow tenant.
-
A footprint is attached to the notes\activities area of the table the file is attached to. This footprint will notify users that the file has been identified as malware, and for more information they should contact their administrator.
- For Microsoft OneDrive, SharePoint Online, Box, Dropbox, or Google Drive:
- The file is now quarantined. Under Events Details, click Quarantine Folder to
navigate to the quarantined folder.




