Procedure
|
|
You must log in to your Secure Access dashboard as an administrator.
|
- Navigate to Connect > End User Connectivity and click Internet Security.
Click the iOS tab.
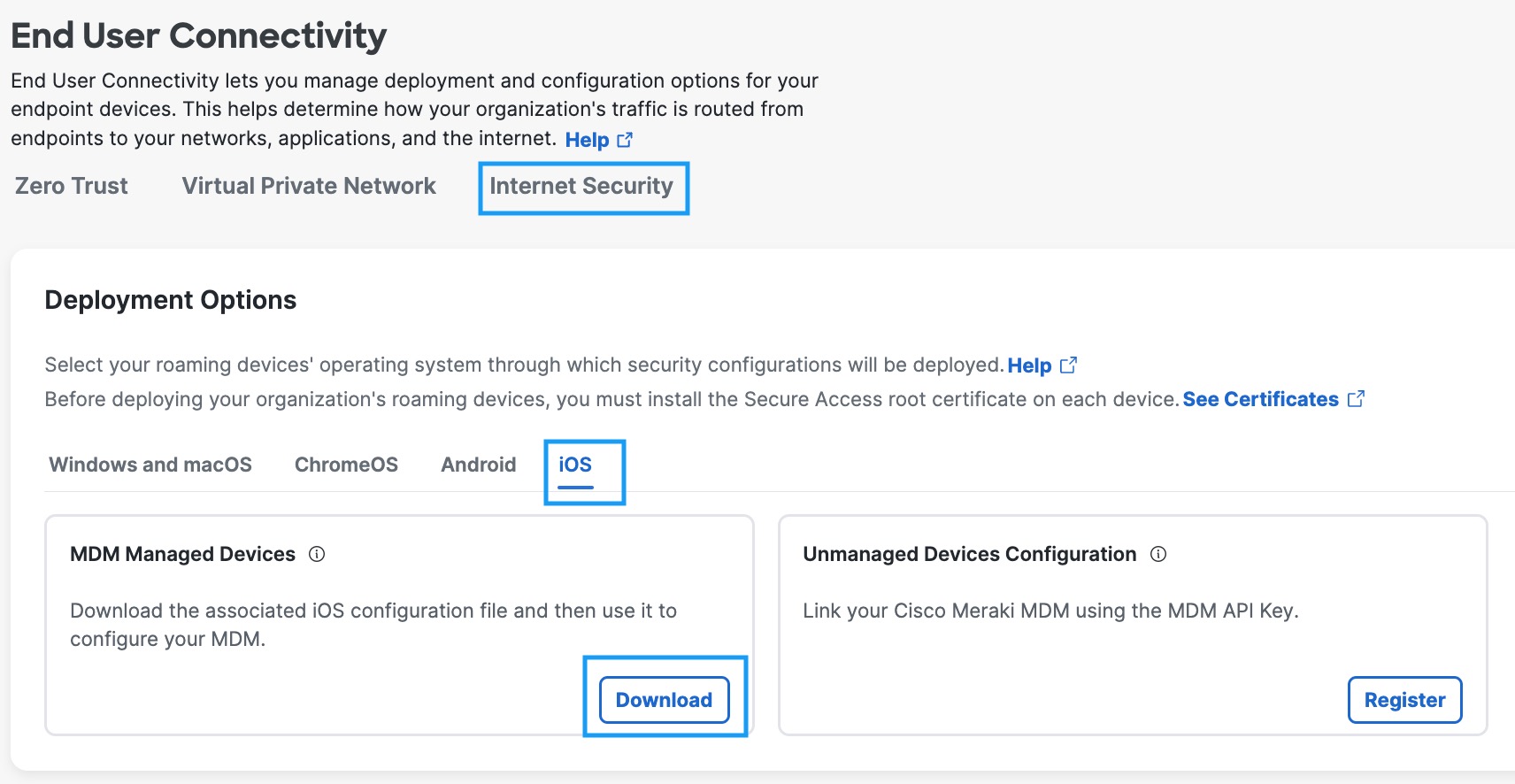
- Under the MDM Managed Devices section, click Download.
- In the Configure Managed iOS Clients window, click Link MDM.

- Add your Meraki MDM API Key, optionally add an Administrator Email, and
click Link.
This email address is where diagnostic reports are sent when a user clicks the I icon from within the iOS device. Once set, this email address is automatically added when managing an MDM.
You acquire a Meraki MDM API key from the Meraki dashboard. For more information, see Cisco Meraki Dashboard API.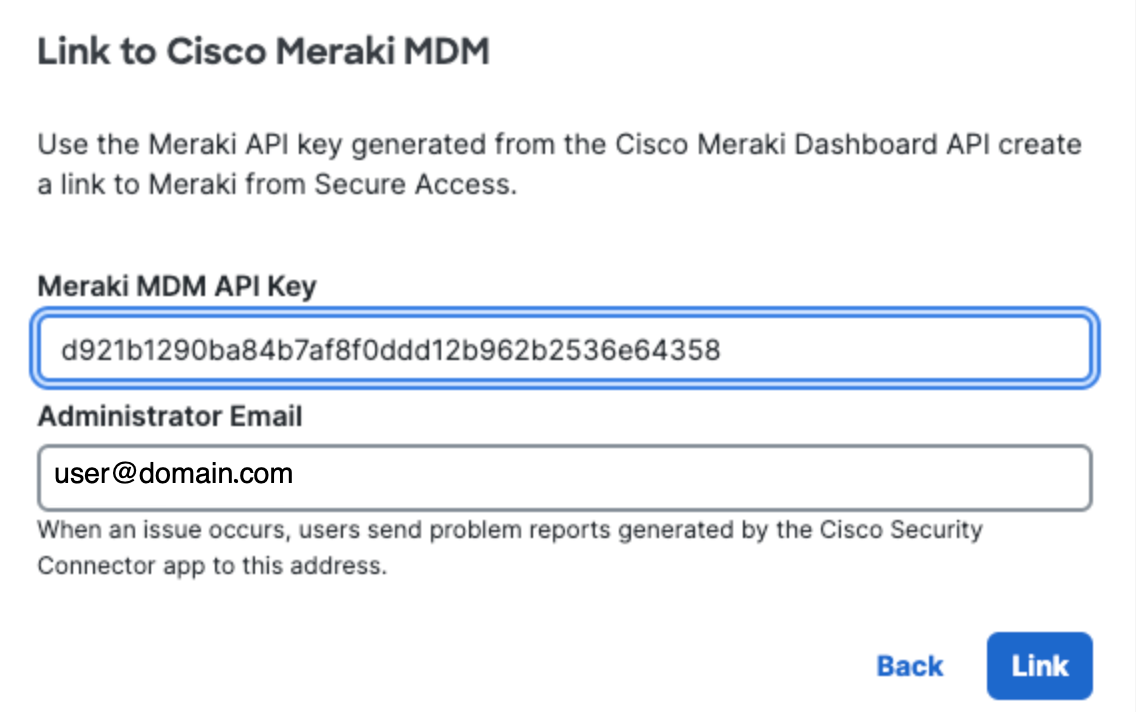
- In the Provision through Meraki MDM modal, select your MDM Profiles.
While you can deploy more than one profile to an iOS device, if you try to deploy more than one profile with Secure Access applied, an error will occur and the second profile will not be applied. You can safely deploy a second profile with only Secure Access applied to a device that has an existing profile that only has Clarity applied.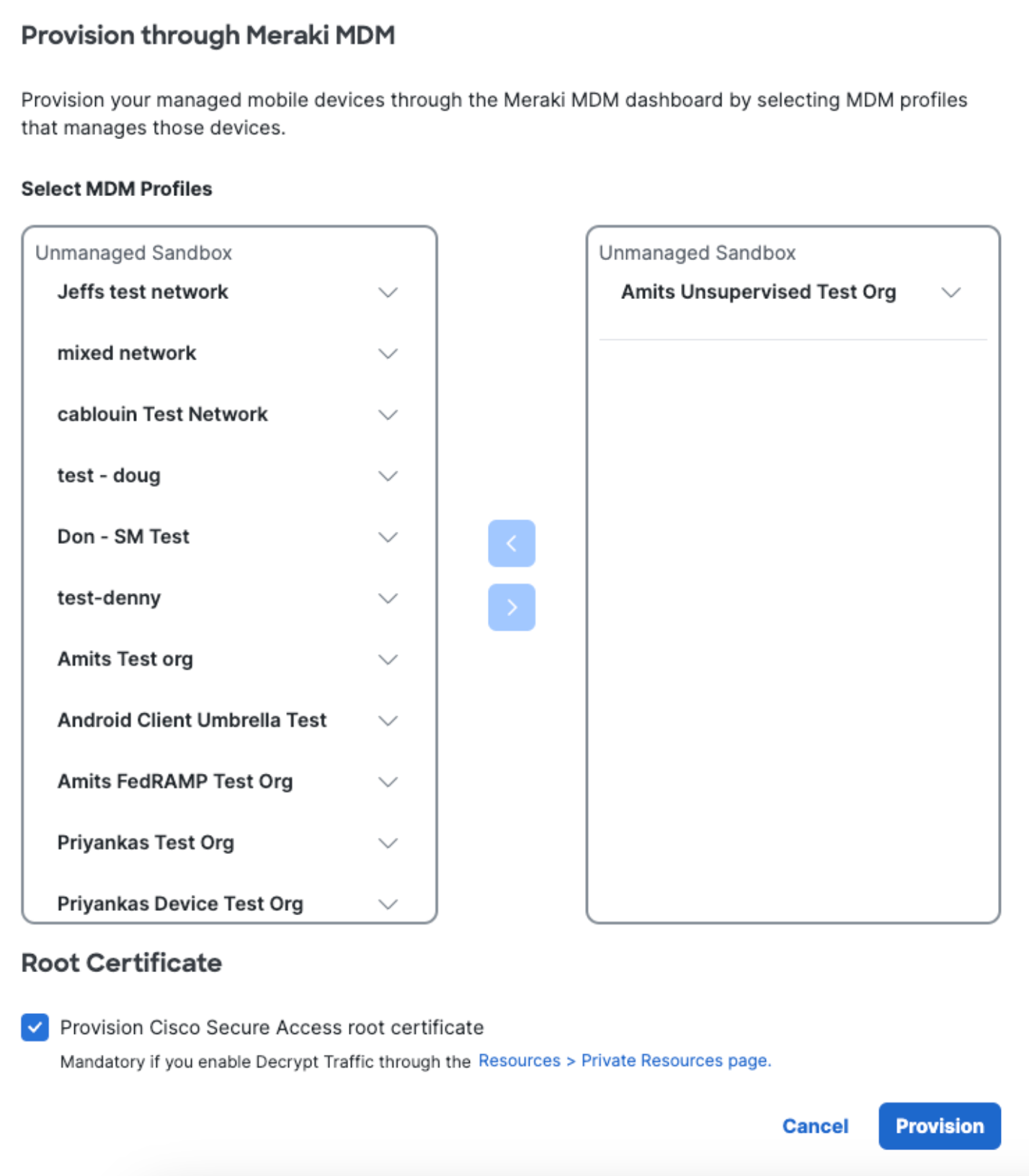
- Check Provision Cisco Secure Access Root Certificate.
The root certificate is required to perform SSL decryption for the intelligent proxy and also helps avoid error messages when visiting blocked pages.
- Click Save.
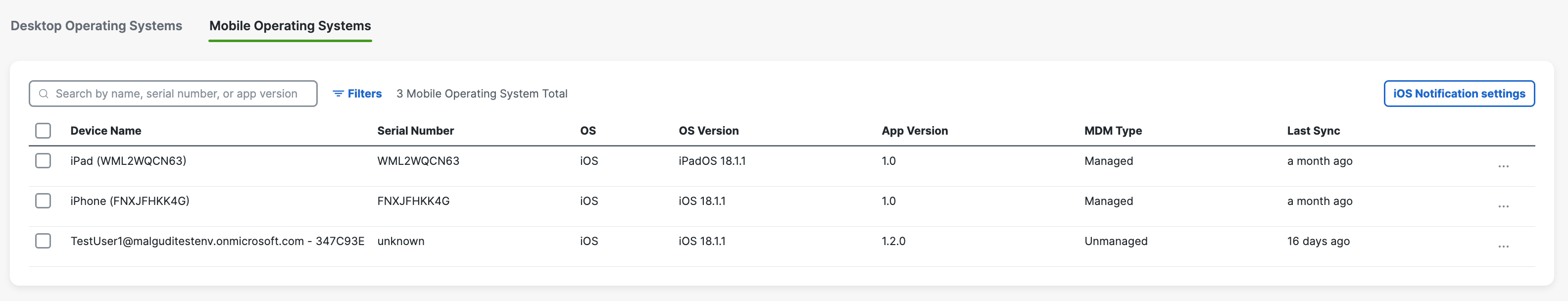
If successful, your mobile device registers with Secure Access and is listed at Resources > Roaming Devices > Mobile Operating Systems. CSC on your mobile device updates to connect to Secure Access so that your iOS device is protected by Secure Access.