Configure Site-to-Site VPN
You can now configure the site-to-site VPN.
- Navigate to Devices > VPN > Site to Site > Add VPN > Secure Firewall Threat Defense Device.
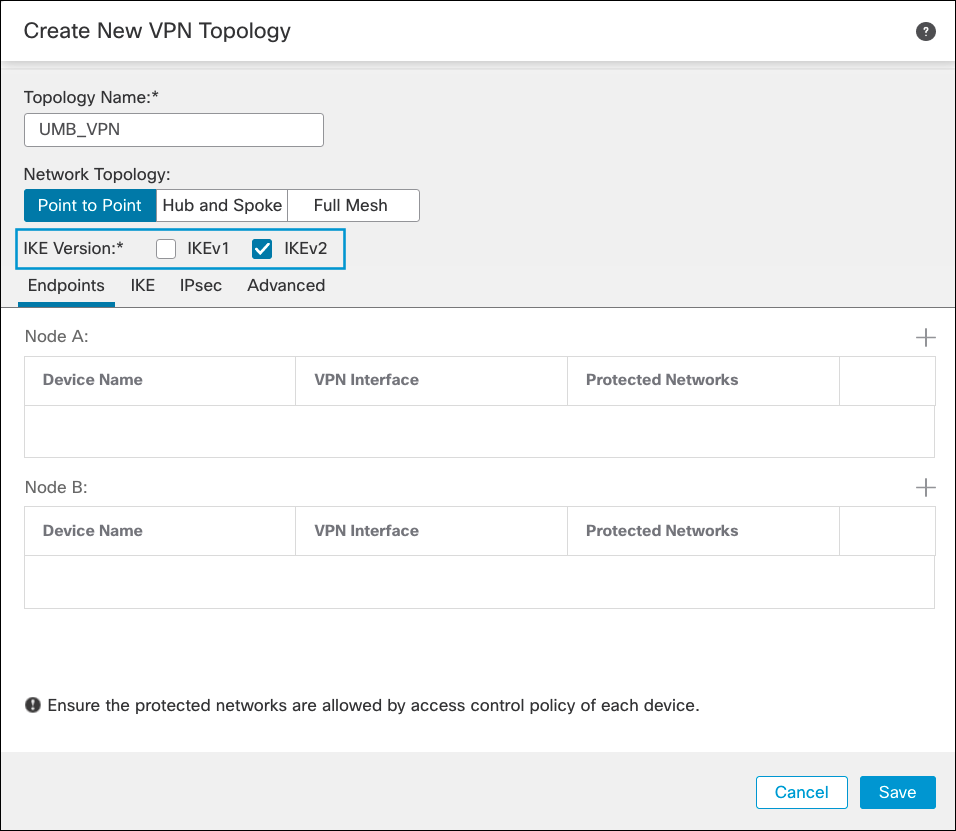
- Enter a name for the topology. Check IKEv2 box (Secure Access supports IKEv2 only). For more information about supported protocols, see Supported IPSec Parameters.
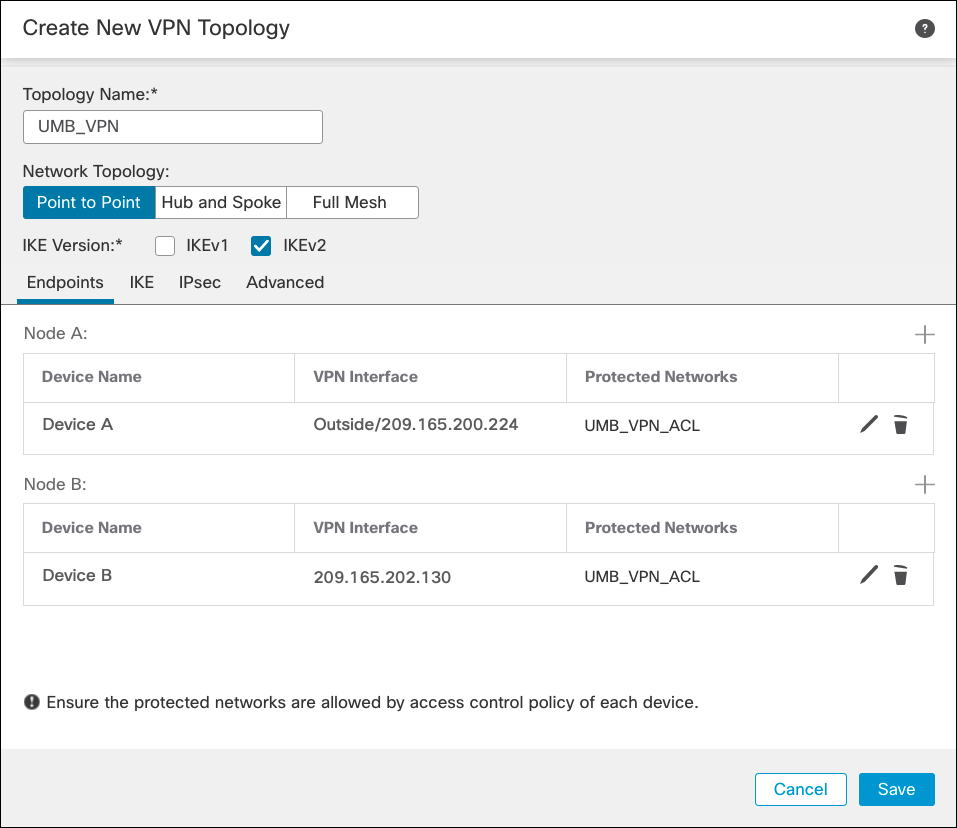
- Add two peers: the local peer (FTD device) and the remote peer (Secure Access).
-
Click Add for Node A and select the FTD device as the local peer and the interface sourcing the IPSec connection. The IP address is automatically populated.
-
Under Protected Networks, select Access List (Extended), and then select the ACL you created in the Traffic Selector ACL . Click OK.
-
Click Add for Node B to add the remote peer.
-
Select Extranet and enter a name. Select Static, and enter one of the Secure Access datacenter IP addresses. Then select the same ACL, then click OK.
-
- Click the IKE tab to add a new IKEv2 Policy containing the desired crypto algorithms. For more information about encryption supported by Secure Access, see Supported IPsec Parameters.
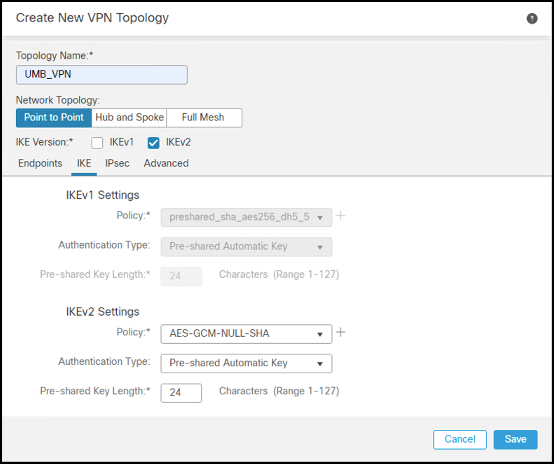
- Enter a name for the IKEv2 policy, then select the parameters from the Supported IPsec Parameters.
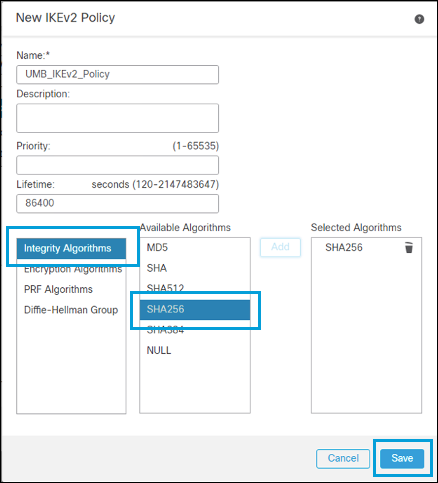
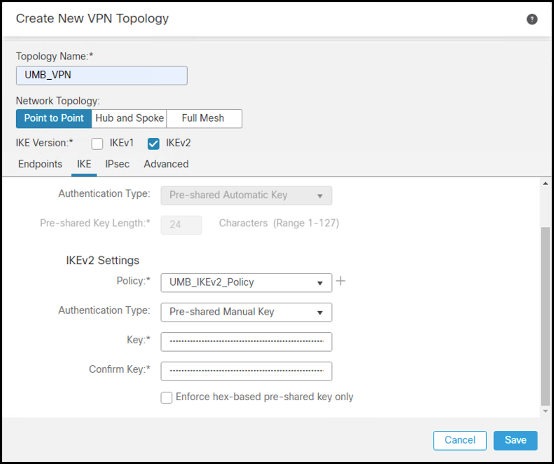
- After saving the IKEv2 Policy, select it. Choose Pre-shared Manual Key from the Authentication drop-down menu and enter the key.
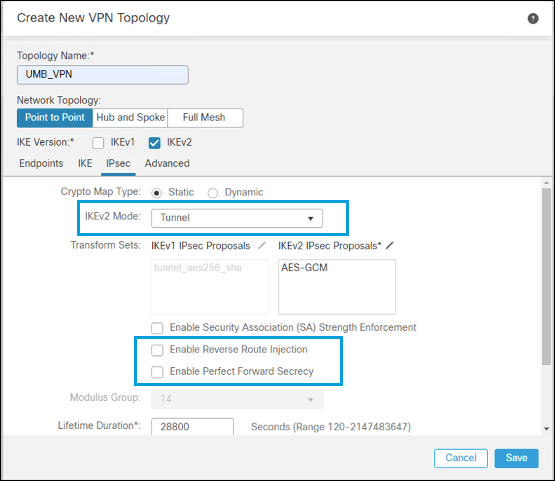
- Under IPSec Configuration, add a new IKEv2 IPsec Proposal with your crypto algorithms or select an existing profile. Select Tunnel for IKEv2 Mode and uncheck Enable Reverse Route Injection and Enable Perfect Forward Secrecy.
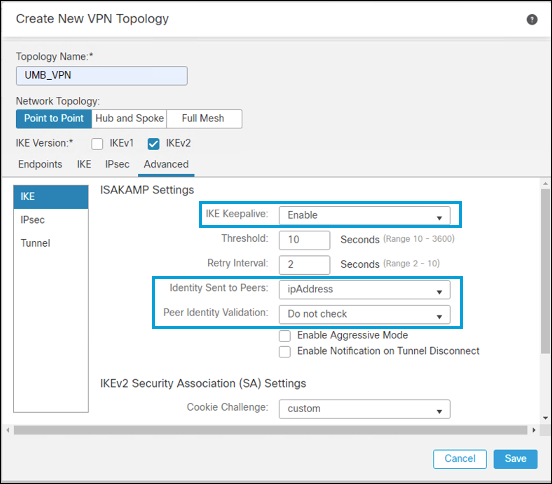
- In the Advanced tab under IKE, enable IKE Keepalive. Select ipAddress as the Identity Sent to Peers, and disable Peer Identity Validation.
- Under IPSec, select Enable Fragmentation Before Encryption, then click Save.










