Step 3b – Add Secure Access Service Provider Metadata to Duo Security
Configure Secure Access as a generic SAML 2.0 service provider application for Duo Single Sign-On. Add the Secure Access service provider metadata to Duo, then download the IdP metadata file from Duo to finish configuring Secure Access in the next step.
Contact Duo Security for assistance. For more information on configuring your IdP, exporting your IdP metadata, obtaining your IdP details, or downloading your IdP's signing certificate, refer to Duo Security documentation.
To automatically configure the generic SAML Duo Single Sign-On application, use the Metadata Discovery option in Update Your Cloud Application in Duo. Upload the Secure Access service provider metadata file Cisco_SSE_SP_Metadata to the Duo Single Sign-On app.
To manually configure the generic SAML Duo Single Sign-On application, extract the EntityID and AssertionConsumerService URLs from the Secure Access metadata and add these to the applicable fields in Duo Security:
- Sign in to the Duo admin portal and navigate to Applications > Protect an Application.
- Search for Generic Service Provider and select 2FA with SSO hosted by Duo.
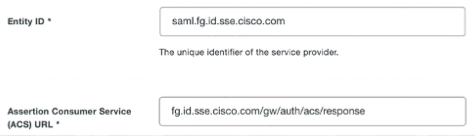
- For Entity ID, enter saml.fg.id.sse.cisco.com and for Assertion Consumer
Service (ACS) URL, enter fg.id.sse.cisco.com/gw/auth/acs/response.
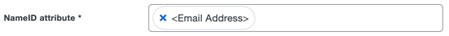
- Enter an email address in the NameID attribute field.
- For Map attributes, configure the IdP attributes.
- Display name—Enter the name you want to display.
- Email Address—Enter an email address.
- First Name—Enter the first name.
- Last Name—Enter the last name.
- Username—Enter the user name.

- Click Save.
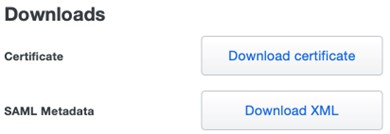
- Click Download certificate to download the certificate, and then click Download XML to download the SAML Metadata file.