Overview
Microsoft Azure supports several methods of connecting to its VPN Gateway. The S2S VPN topology depends on components configured in the following order. Components in the diagram are numbered by order of configuration.
- An Azure virtual network with a VPN gateway in active-active mode for tunnel redundancy. In active-active mode, Azure provides two VPN gateway IPs that Secure Access can use to establish a network tunnel group. Traffic will use the primary tunnel. In the event of a tunnel failover, the switch to the secondary tunnel will be automatic, immediate, and without interruption.
- A Secure Access network tunnel group with two IPsec/IKEv2 tunnels and a pre-shared key (PSK) for connection with the Secure Access cloud native head end (CNHE) service.
- Two local network gateways in Azure that establish S2S connections between the Azure VPN Gateway client and the Secure Access CNHE.
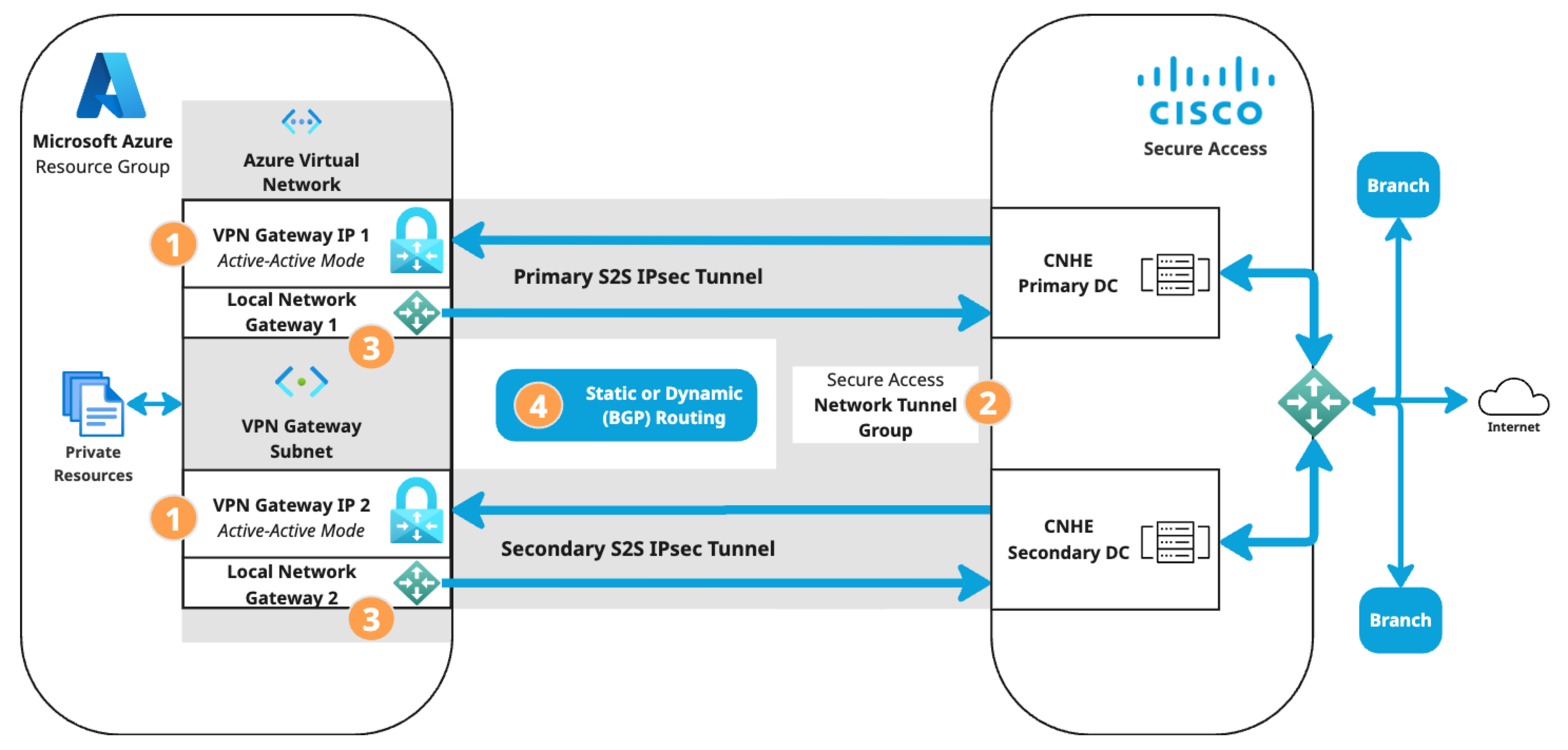
- Branch and internet routing.
-
The static routing use case requires an Azure VPN Gateway route table.
-
The dynamic routing use case requires an Azure VPN Gateway autonomous system number (ASN) and Azure local network gateway BGP peer IP addresses.
-
For more information about VPN and tunnels in Secure Access, see Manage Virtual Private Networks and Manage Machine Tunnels.
For more information about Azure, see Microsoft documentation:
- What is Azure VPN Gateway?
- Azure VPN Gateway topology and design: Site-to-site VPN
- Design highly available gateway connectivity for cross-premises and VNet-to-VNet connections: Active-active VPN gateways
- Tutorial: Create a site-to-site VPN connection in the Azure portal
- Azure: Create, change, or delete a route table
- Azure: BGP and routing
|
|
Microsoft may update their documentation without notice.
|

