Procedure
Before you begin
- Ensure your Chromebook is updated to Version 126 or later versions. For more information, look for the 'DEVICE_IP_ADDRESSES' term in the DnsOverHttpsTemplatesWithIdentifiersdocumentation.
- Ensure that your Chromebooks are configured with a Managed Network as the 'DEVICE_IP_ADDRESSES' variable is supported only for Managed Networks. For more information on setting up Managed Networks, see the Set up networks for managed devices guide.
Procedure
| 1 |
From Secure Access, navigate to . |
||
| 2 |
On the End User Connectivity page, click the Internet Security
tab. |
||
| 3 |
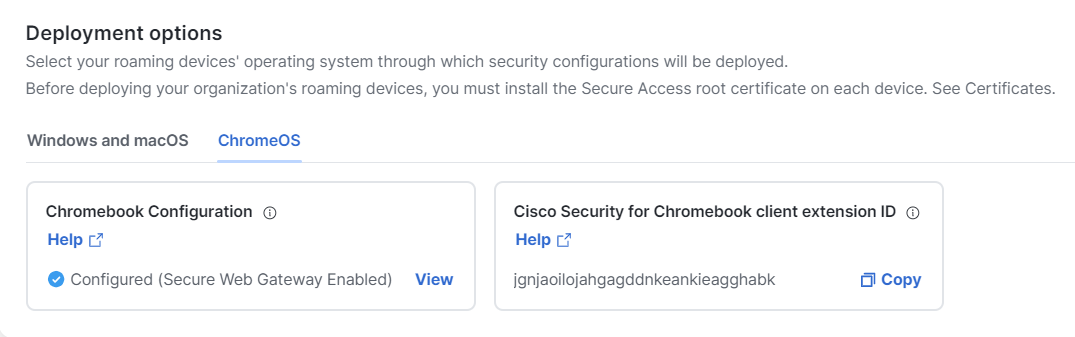
In the Deployment options section, click the ChromeOS tab. |
||
| 4 |
In the Chromebook Configuration section, click View. |
||
| 5 |
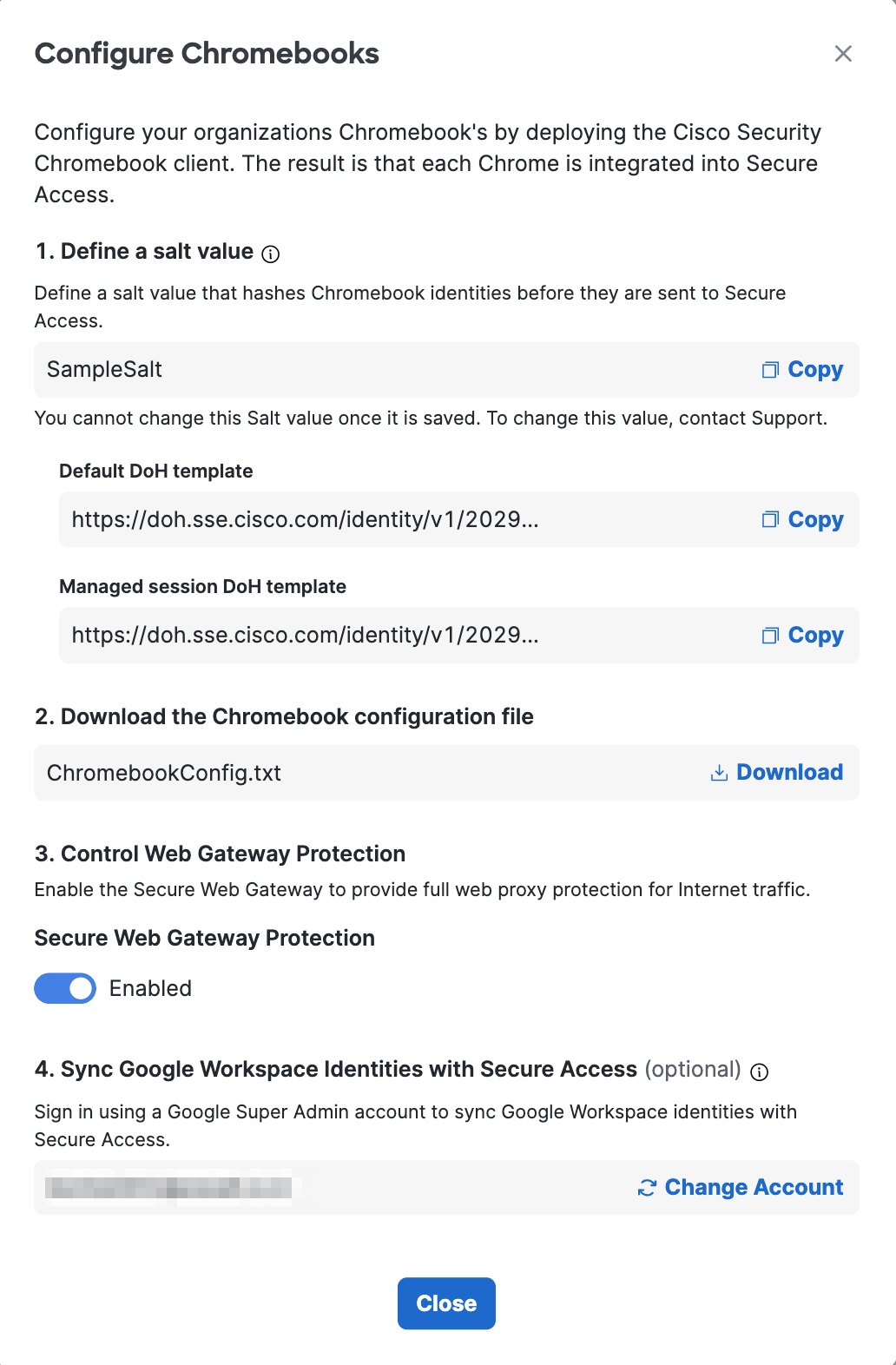
In the Configure Chromebooks window, click Copy to take a copy of the necessary DoH template URL. Then, add the 'DEVICE_IP_ADDRESSES' placeholder into the DoH template as illustrated in the example URLs below: Default DoH Template:
Managed Guest/Public Session DoH Template:
|
||
| 6 |
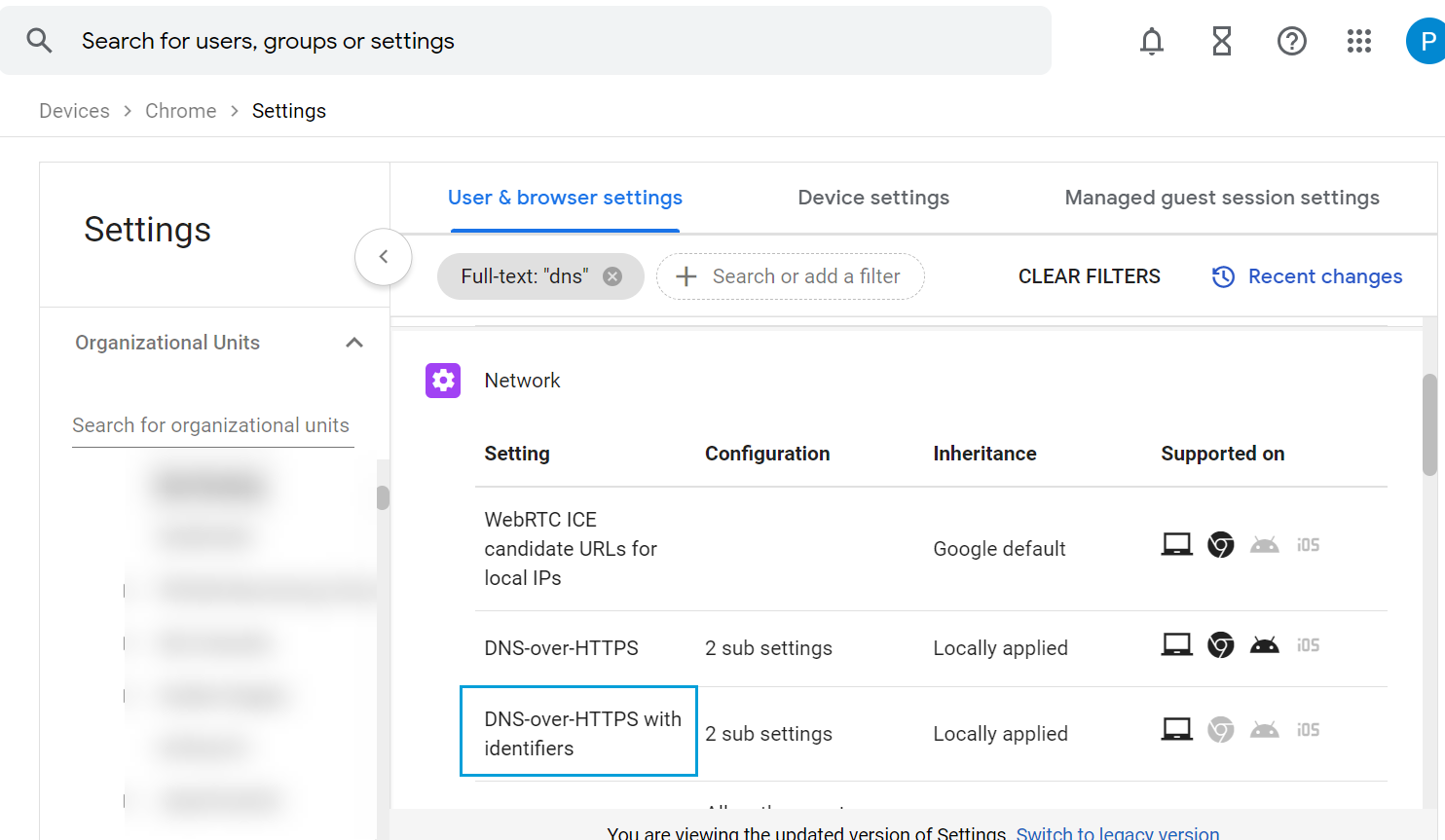
In the Google Admin
console, navigate to , choose the organizational unit (OU) on which you want to apply the
template configuration, and select DNS-over-HTTPS with
Identifiers. |
||
| 7 |
Enter the updated DoH template to the OU.
After updating the DoH template, your Chromebook device is configured to report their private IP addresses to Secure Access. For assistance, contact Contact Cisco Secure Access Support. |