Procedure
Before you begin
Procedure
| 1 |
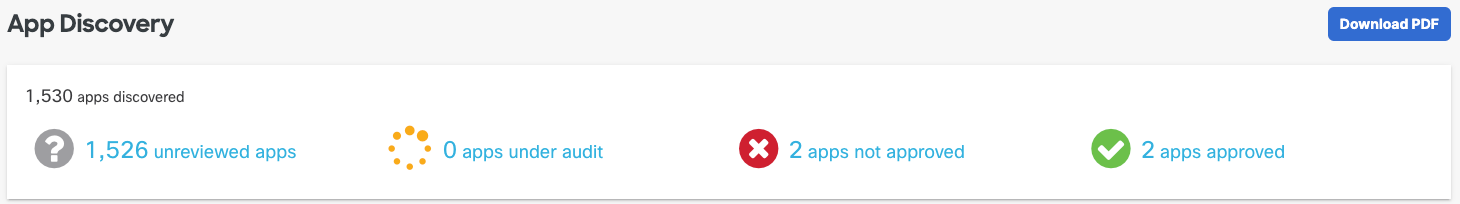
Navigate to and click one of the app labels to open the Apps Grid. |
||||
| 2 |
Click the name of an app to view its details and traffic data for the last 90 days. |
||||
| 3 |
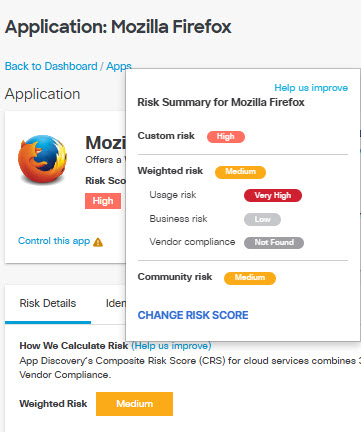
View the initial details of the app, including the name and a description of the
app.
|
||||
| 4 |
Click Risk Details. The Risk Details tab displays the app's risk score and how it was calculated, including Business Risk, Usage Risk, and Vendor Compliance. 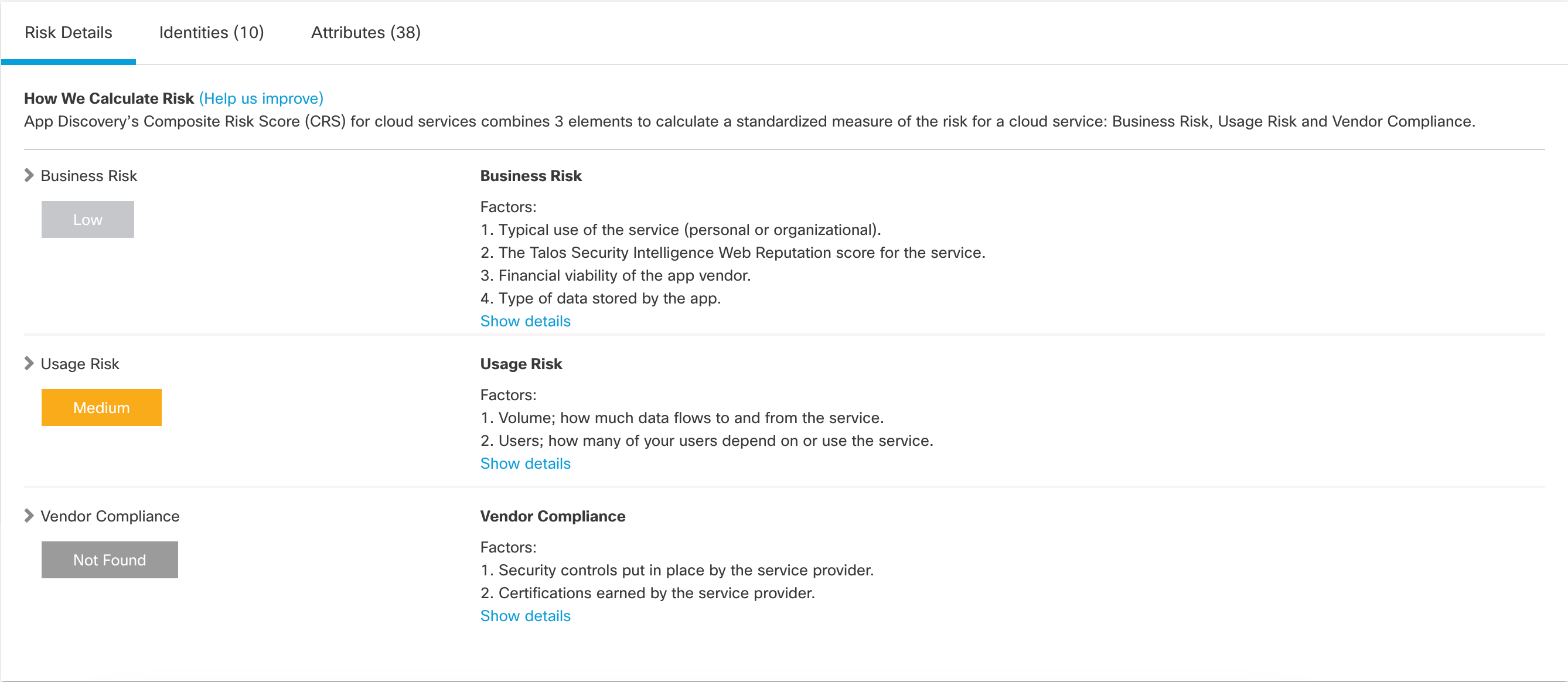
|
||||
| 5 |
Click Identities. The Identities tab lists your organization's sources that have made DNS requests and traffic for this app. Click the Download CSV icon to download this information as a CSV file. 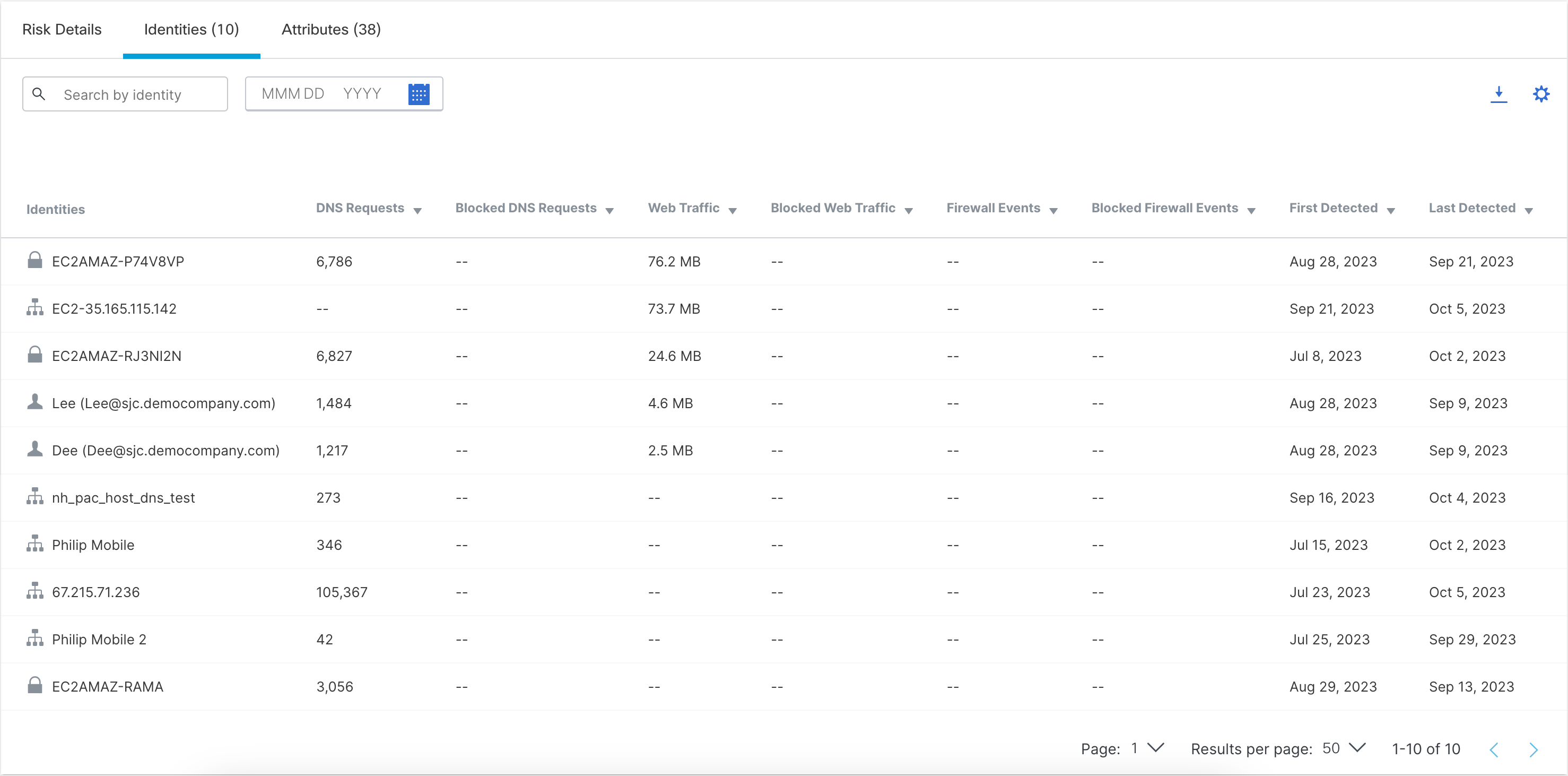
|
||||
| 6 |
Click Attributes. The Attributes tab lists the various attributes associated with this app. 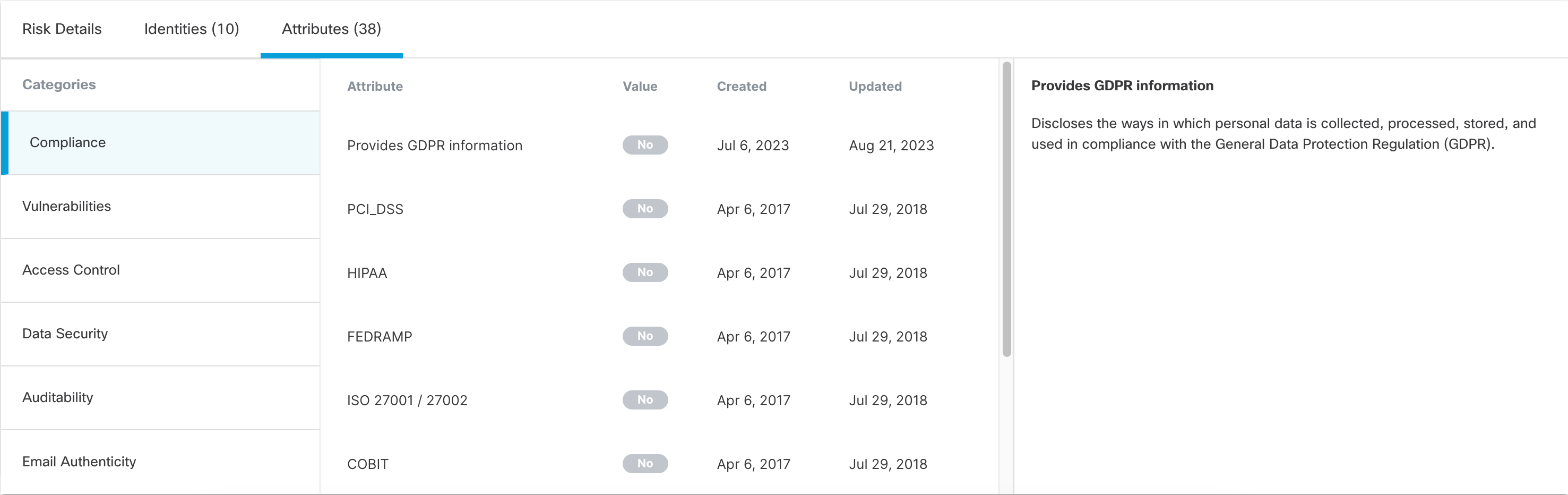
Attributes are divided into categories. Click a category name to view the attributes associated with it. (Not all applications will show all attribute categories.) For each displayed attribute, Secure Access shows whether the attribute applies to the application and the dates when the attribute information was collected and updated. Use the attributes to evaluate the risk that the application will expose your environment to data breaches, identity theft, financial fraud, and other cyber threats. The attribute categories are:
|