Step 2 – Select Okta SAML Identity Provider in Secure Access
In the SSO authentication profile, select the Okta SAML IdP, copy the metadata URL for the Secure Access service provider, and choose the time interval when end users will authenticate with Secure Access.
- For Identity Provider, choose Okta.
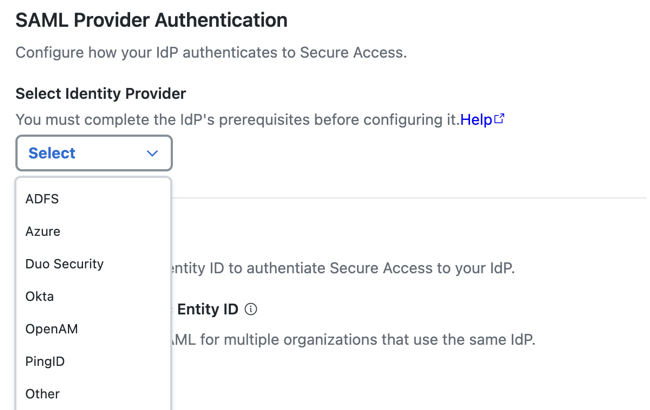
- (Optional) Enable an organization-specific entity ID.
-
Organization-specific Entity ID—Choose this option when you have multiple
Secure Access organizations and need to configure SAML authentication for Secure Access
Internet Security and Zero Trust Network Access (ZTNA) for these organizations against
the same IdP. The Secure Access SAML default common
EntityIDis saml.fg.id.sse.cisco.com. Secure Access allows you to override the default Secure Access SAML EntityID for each organization.
-
Organization-specific Entity ID—Choose this option when you have multiple
Secure Access organizations and need to configure SAML authentication for Secure Access
Internet Security and Zero Trust Network Access (ZTNA) for these organizations against
the same IdP. The Secure Access SAML default common
- For Entity ID URL, click Copy URL.
Save the Secure Access metadata URL in your local environment. The Secure Access SAML default common
EntityIDis saml.fg.id.sse.cisco.com.
Use the Secure Access SP metadata URL to configure the Okta SAML IdP app integration. For more information, see Configure Okta with the Secure Access SAML Metadata.
- Choose a time interval when a user must authenticate with Secure Access, or select
Never.
The time intervals are: Daily, Weekly, or Monthly.
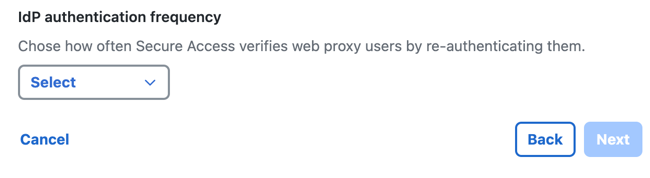
- Click Next.



