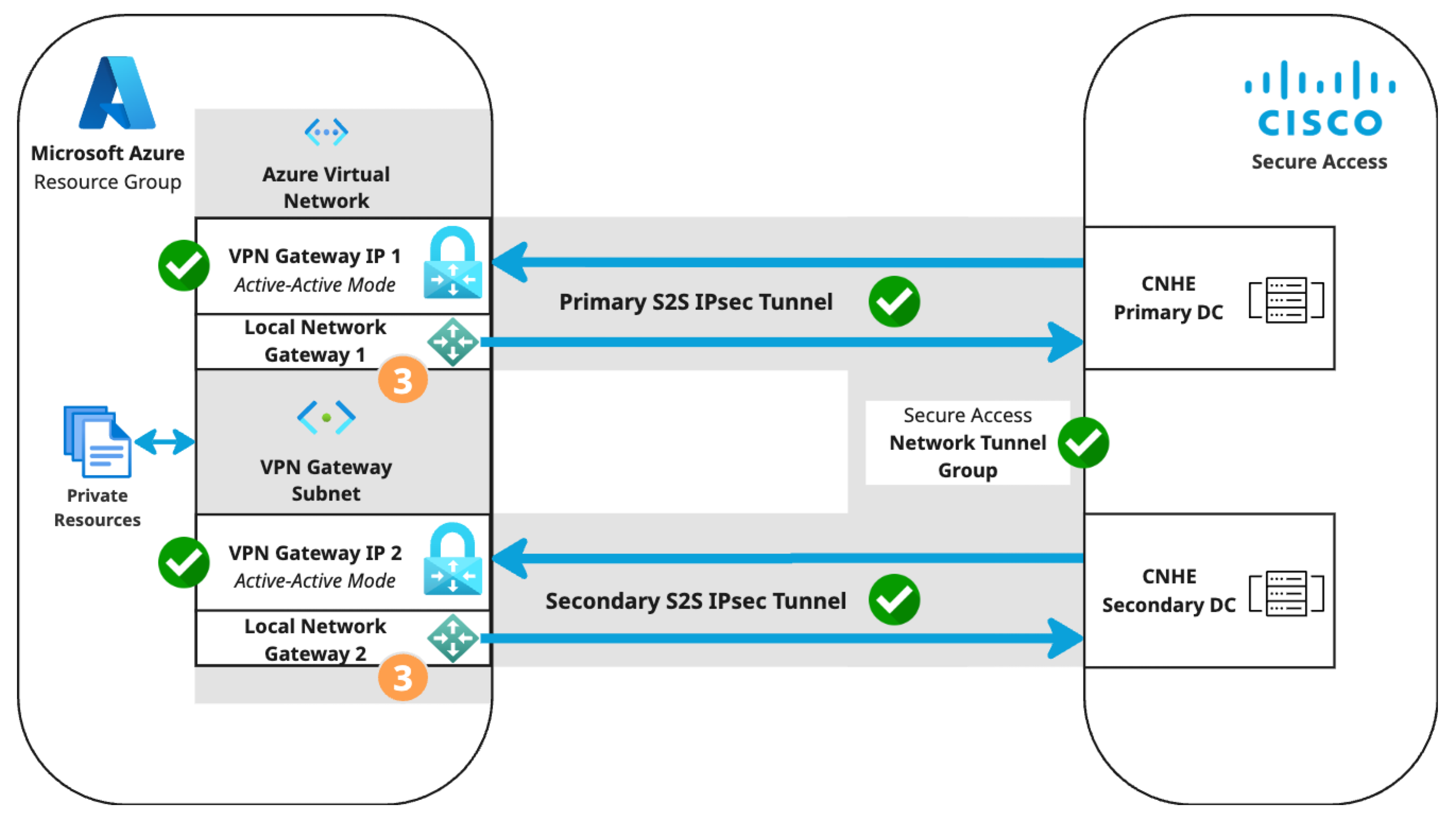
Step 3: Create two local network gateways in Azure with S2S connections
Create and configure two local network gateways in Azure, then connect them to Secure Access. The local network gateway acts as the remote site connected by tunnel to the Secure Access CNHE DC.
- In the Azure admin portal, navigate to Overview > Resource group (click the name of your resource group) > + Create.
- Search the marketplace for Local network gateway, then click Create.
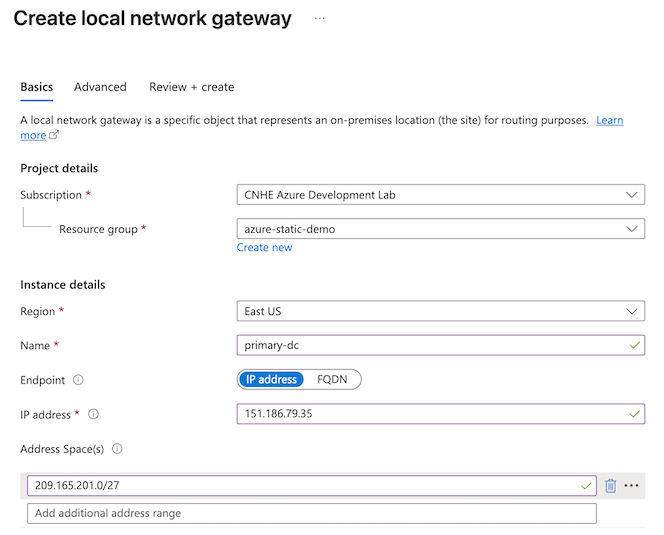
- Configure the Basics tab of the first local network gateway.
- Select the Subscription and Resource group of your virtual network.
- Name: This example uses primary-dc.
- Endpoint: IP address
- IP address: For the first local network gateway, enter the Primary DC IP Address from Secure Access Step 4 - Data for Tunnel Setup.
- Address Space(s): Add one or more IP ranges for branch sites that will connect to the Secure Access network tunnel group. Address spaces should not overlap with other IP ranges in your network. This example uses 209.165.201.0/27.
-
-
Review the configuration, then click Create. Azure will deploy the local network gateway and update the dashboard with the local network gateway resource when deployment is complete.
- Repeat step 3 to create the secondary local network gateway with the Secondary DC IP Address from Secure Access.

- Create the S2S connection for the primary local network gateway.
- In the Azure admin portal, navigate to Overview > Resource group (click the name of your resource group) > Resources, then click the name of your virtual network gateway.
- Navigate to Connections, then click + Add.
- Configure the Basics tab of the connection.
- Select the Subscription and Resource group of your virtual network.
- Connection type: Site-to-site (IPsec).
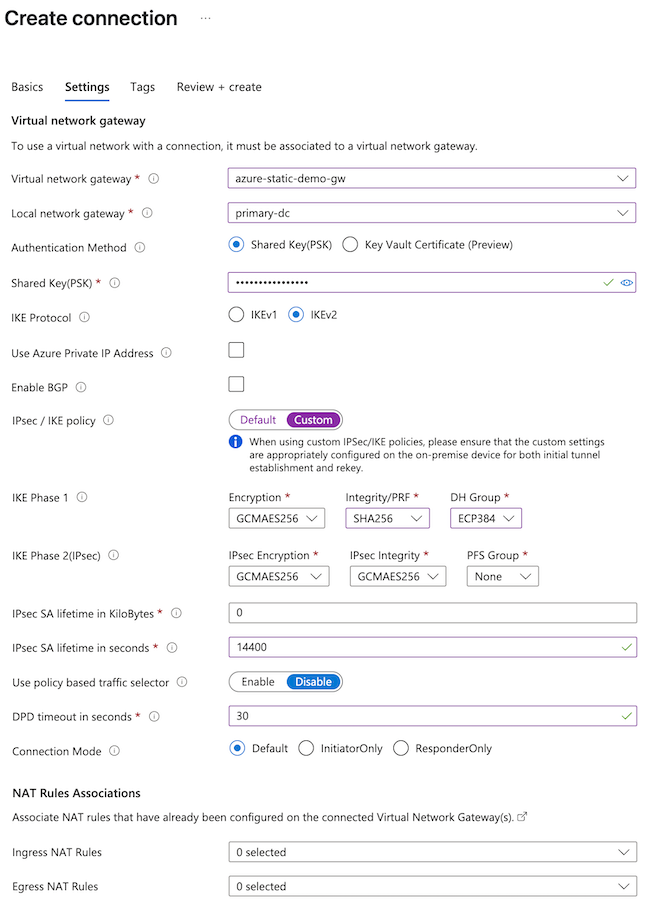
- Configure the Settings tab of the connection.
- Select your virtual network gateway.
- Local network gateway: Select the primary gateway.
- Shared Key (PSK): Enter the passphrase configured for the Secure Access network tunnel group in step 2.
- IPsec / IKE policy: Custom.
-
IKE Phase 1: The following configuration is recommended.
- Encryption: GCMAE256.
- Integrity/PRF: SHA256.
- DH Group: ECP384.
- For information about cipher parameters supported by Secure Access, see Supported IPsec Parameters. For information about cipher parameters supported by Azure, see Microsoft documentation on Default IPsec/IKE parameters.
- IPsec SA lifetime in seconds: 14400
- DPD timeout in seconds: 30
-
Review the configuration, then click Create. Azure will deploy the S2S connection and update the dashboard when deployment is complete.
- Repeat step 5 for the secondary local network gateway.
- Both S2S VPN tunnels are now established with static routing between your Azure virtual network gateway and the Secure Access cloud native head end (CNHE) service.