DNS Backoff Settings
Bypass DNS traffic from Secure Access for the following contexts:
- Select Backoff behind Virtual appliance. When enabled and the Cisco Secure Client detects a Secure Access Virtual Appliance (VA), DNS traffic goes through the local network instead of redirecting to Secure Access.
- Select AnyConnect Trusted Network Detection (TND) to disable DNS traffic forwarding from an endpoint to Secure Access if the network is trusted. This setting requires that you have the Trusted Network Detection (TND) setting enabled in the AnyConnect VPN profile for the user devices.
- Select DNS protected network to disable DNS traffic forwarding while on a network protected by Secure Access. Relies on the protection of the network. To trigger this setting, you must register the public network in Secure Access and add the network to a rule that has a higher priority than the roaming devices. In addition, the local DNS server egress network must have the same network registration as straight out from the computer to 208.67.222.222.
- Select Customer trusted network to disable DNS redirects to Secure Access if the domain name added to the Subdomain field is found on the network and resolves to an RFC-1918 local IP address.
- For Subdomain—enter a domain that Secure Access uses to query the local DNS server.
You must enable Customer trusted network to add the subdomain.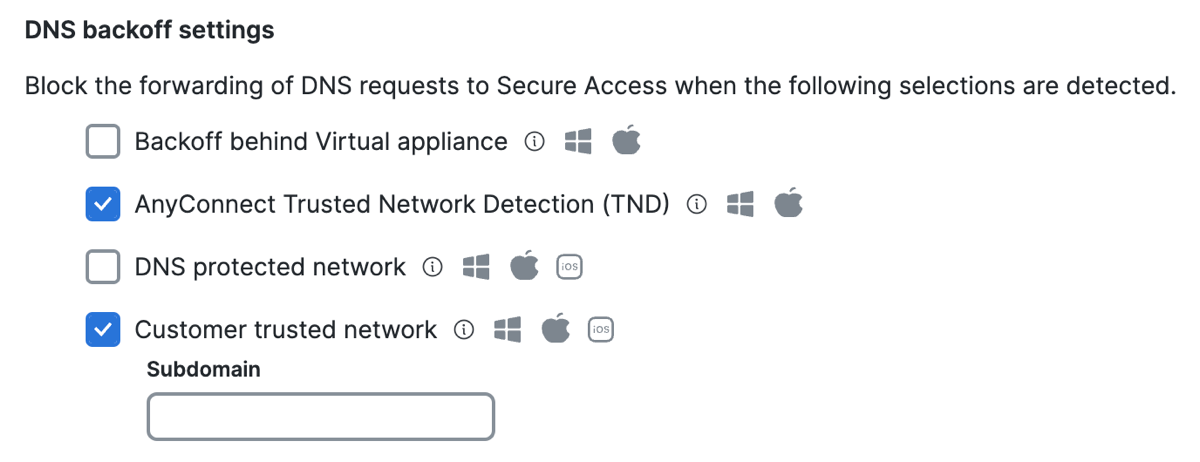
- For Subdomain—enter a domain that Secure Access uses to query the local DNS server.

