Edit a Tenant
You can change the protection type or Response Action you have selected for a tenant.
- Navigate to Admin > Authentication.
- Click to expand Microsoft 365 in the list of Platforms.
- In the Cloud Access Security Broker subsection , from the Edit column, click
Edit. You can edit any tenant.
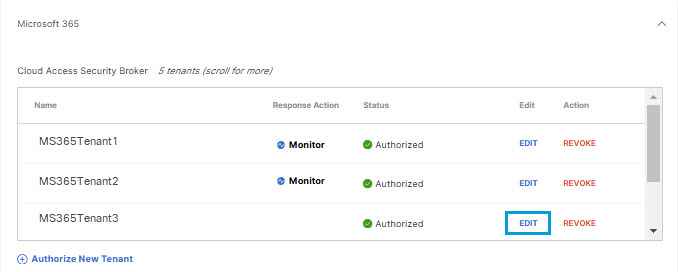
- Choose to authorize your Microsoft 365 tenant for Cloud Malware protection, or detection
of third-party cloud applications, or both.
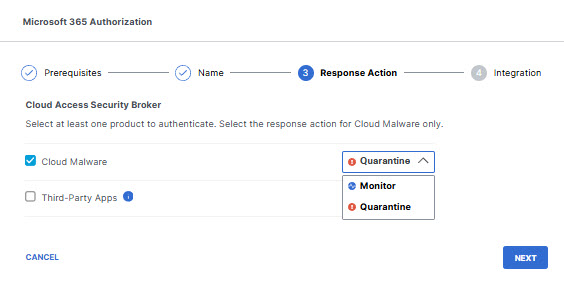
If you choose to authorize for Cloud Malware protection, you must also select a Response Action for Umbrella to apply to Microsoft 365 files found with malware.
-
Choose Monitor to cause Umbrella to log files detected with malware. You will be able to manually quarantine these files from the Cloud Malware report.
- Choose Quarantine to:
-
Move the file into a folder named Cisco_Quarantine_Malware in the root path of the admin who authorized the tenant, remove all collaborators, and change the file owner to the Microsoft 365 admin.
-
Replace the file in its original location with a text file named filename.ppt_Cisco_Quarantined.txt explaining to the original file owner that the file is identified as malware and for more information to contact their organization administrator.
-
If you choose Quarantine this will apply only to rules applied to Sharepoint and OneDrive; Secure Access supports monitoring outgoing Outlook messages, but cannot quarantine them.For more information on Cloud Malware monitoring and quarantine features, see Manage Cloud Malware Protection. For more information on Third-Party Apps detection features, see Third-Party Apps Report.
-
- Click Next.
- The new Response Action is displayed.
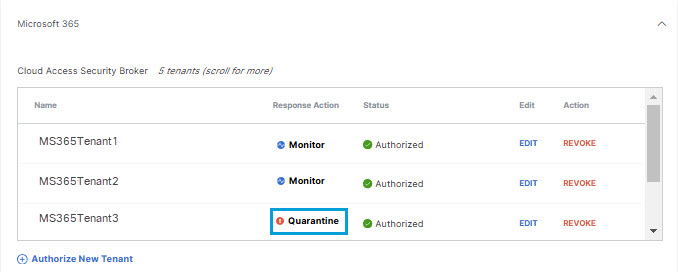
For tenants authorized only for CASB detection of third-party applications, no Response Action is shown.




