View Events
- Navigate to Monitor > Reports > Data Loss Prevention.
- On the Events tab, select a time frame to view reports generated in a specific date
range. You can also choose a custom date range.
- Use the available Filters for better search results; choose from those listed
below:
File Size—Indicates the size of the file that triggered the event.
Event Type—Indicates the type of rule that triggered the event: Real Time (for private or internet resources), SaaS API, or AI Guardrails.
Action—The action the system has applied to the content: blocked, deleted, monitored, quarantined, restored from quarantine, revoked access.
Severity—The severity of the rule that triggered the event.
Application—Application for which an SaaS API rule is applied.
Exposure—Exposure of the content scanned.
Identity Type—The type of identity involved in the event.
Application Categories—The category of the application involved in the event. This filter displays only events that occurred after this filter was added to Secure Access, in January of 2024.

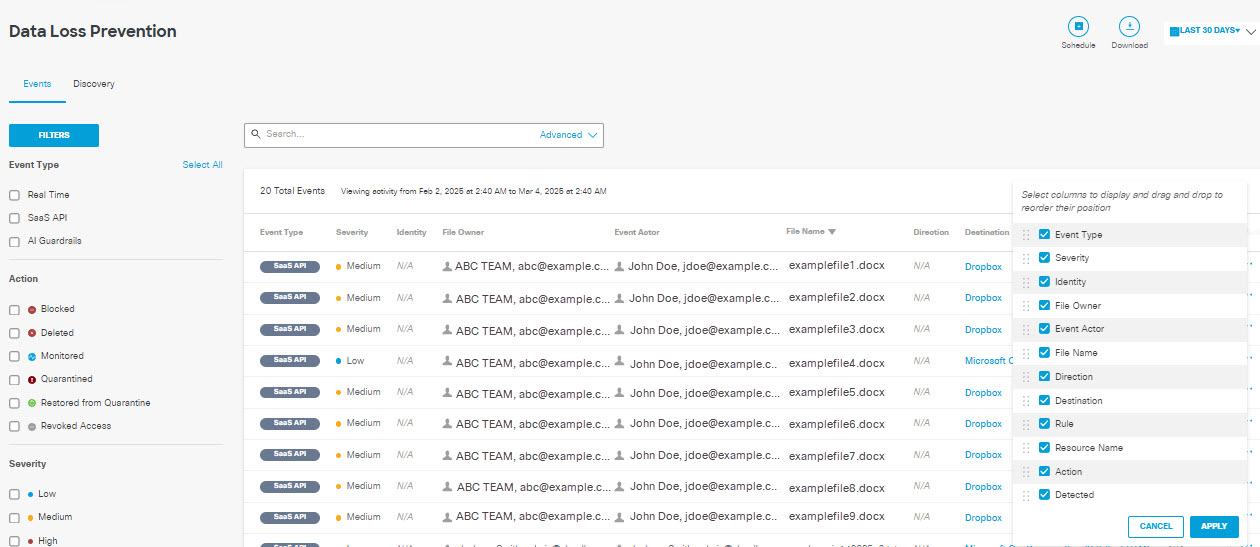
- Click the gear icon to customize and sort the columns of your report.
Event Type— Indicates the type of rule that triggered the event: Real Time, SaaS API, or AI Guardrails.
Severity—The severity of the rule that triggered the event.
Identity—The identity that made the request.
File Owner—The owner of the file that created the violation in the vendor.
Event Actor— The user who performs an action that triggers a rule violation.
File Name—The name of the file or attachment where a classification match was found. (This includes attachments to Outlook email messages.) When content is found in a message, a post, or form data, the File name displays Message, Content, or Form.
Destination—The destination where the content was scanned.
Rule—The rule that triggered the event.
Resource Name—For AWS S3 this displays the S3 bucket associated with the content that triggered the violation. For Azure Storage this displays the storage account or container associated with the content that triggered the violation. For other applications, this displays "N/A."
Action—The action triggered by the rule on detecting a violation.
Detected—The date and time of detection.
- Click the action menu icon (three dots) to view further details of an event. See View Details



