Add Network Object
Create a network object type “Group”. You will use this object in NAT configuration as well as in the Access Control List (ACL) in the IKEv2 traffic selector. Using a group object simplifies the task of bypassing encryption and provides NAT for the bypassed traffic.
|
|
Public IP traffic from SIG users will appear to come from the address ranges 146.112.0.0/16 and 155.190.0.0/16. Depending on your organization, you may be required to inform service providers that you access through the Secure Access service of these additional IP address ranges. For example, some service providers require prior knowledge of the IP address ranges used before allowing access to their service.
|
- Navigate to Objects > Object Management > Network > Add Network > Add Group.
- Add the Secure Access resolvers IP address so the DNS queries are not sent through the tunnel.
Currently, if the DNS queries are sent through the tunnel it will be NATed to 146.112.0.0/16 IP range and queries will not be linked to the user's dashboard. By bypassing the traffic to the Secure Access resolvers it is possible to add a public IP address to the dashboard (network deployment) and retrain DNS visibility and enforcement capabilities.
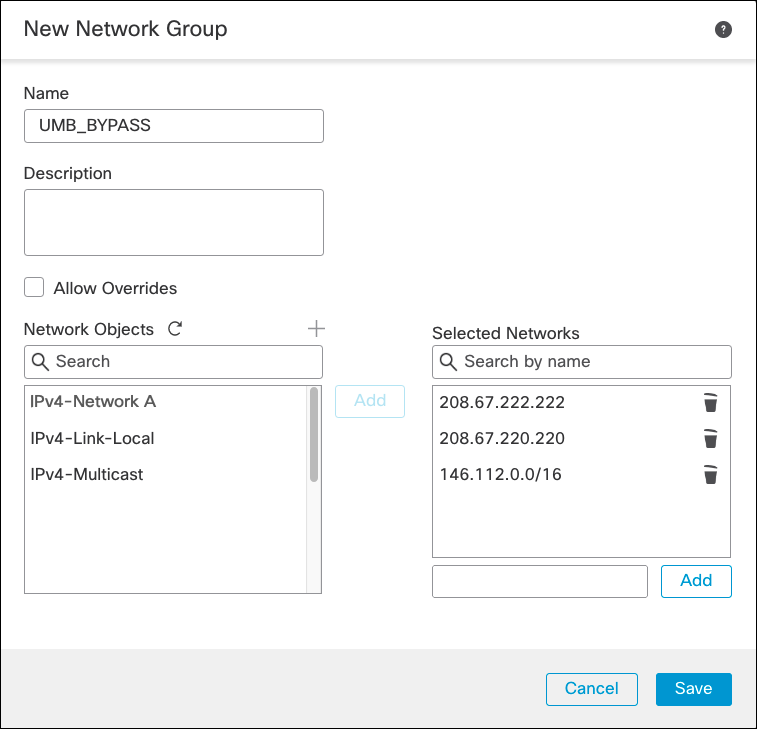
- Optionally, add 146.112.0.0/16 as a network. Web traffic from endpoints with PAC file or Cisco Secure Client as well as proxy chaining traffic can then go outside the IPSec tunnel and achieve higher throughput.

