Reusable Destinations in Internet Access Rules
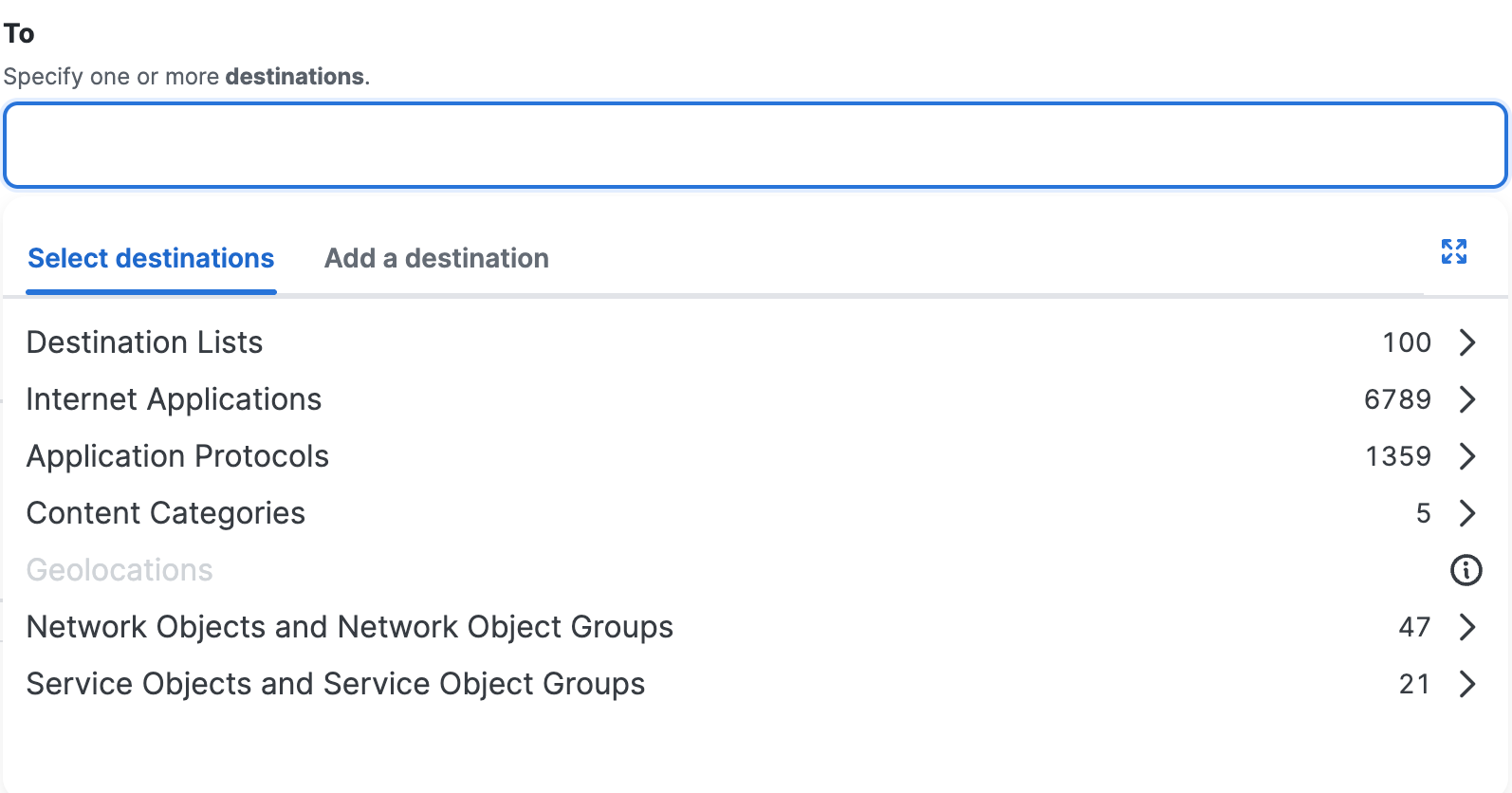
- Destination Lists - List groups of domains, URLs, IP addresses, and CIDR blocks to which you want to apply the same policy. You can create custom lists of destinations based on any criteria you choose.
- Content Category Lists - Create lists of web sites based on the content or type of the site, so you can control access to a variety of sites as a group. For example, you might create a content category list that includes all sites belonging to the Adult, Child abuse, and Pornography categories.
- Application Lists - Create lists of web-based applications to which you want to apply the same policy. For example, if you want to apply a single policy to all social media applications, you can create an application list that includes all applications in the Social Networking category.
For some web-based applications, you can allow access to the application, but block uploads, downloads, and posting or sharing information. You will see these options in each rule when you configure applicable destinations in the rule. For details, see Advanced Application Controls.
- Network Objects - Network Objects represent IPv4 and IPv6 addresses, CIDR blocks, ranges of IPv4 addresses, wildcard masks, or fully-qualified domain names (FQDNs). Select the Network Objects on the access rules to apply security controls to the traffic on the networks.
- Network Object Groups. Select the Network Object Groups on the access rules to apply security controls to the traffic on the networks in groups.
- Service Objects - Service Objects represent a port, range of ports, protocol, or traffic on any protocols. Select the Service Objects on the access rules to apply security controls to the services.
- Service Object Groups - Select the Service Object Groups on the access rules to apply security controls to the traffic on the services in groups.
