Summary Reports for Security Compliance
Cisco Security Risk Score Summary
Cisco Security Risk Score Summary provides the risk assessment of your workloads based on the Cisco Security Risk scores. The Cisco Security Risk Score graph displays the number of workloads with high, medium, and low severity CVEs. The CVE's Risk Details graph displays the number of CVEs for each of the supported attributes of Cisco Vulnerability Management.

The downloaded compliance report lists top 10 workloads with CVEs of high severity status based on the Cisco Security Risk Score.
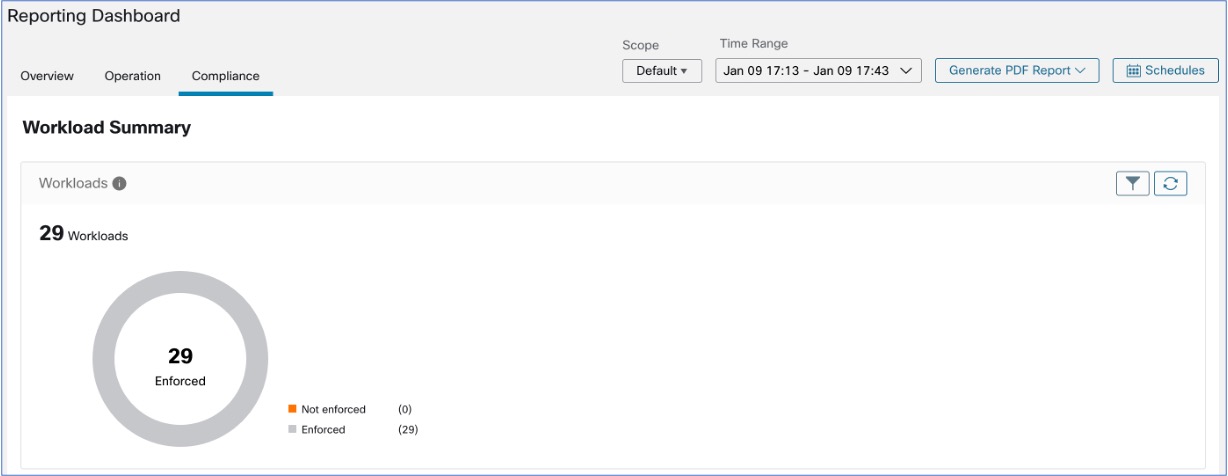
Workload Summary
Workload Summary provides a view of the total agents that are deployed on one or more servers and endpoints in the infrastructure. The agents monitor and collect network flow information, enforce security policies with firewall rules on the installed hosts, communicate the status of the workload and receive updates on the security policies.
Security Summary
Configure your forensic events; once configured, all tactics are displayed without any rules under them, with a count of 0. Select one or more forensic rules to make the selection at the tactic level. Selecting a tactic selects all the rules under it. Default MITRE ATT&CK rules are provided to alert techniques from the MITRE ATT&CK Framework.

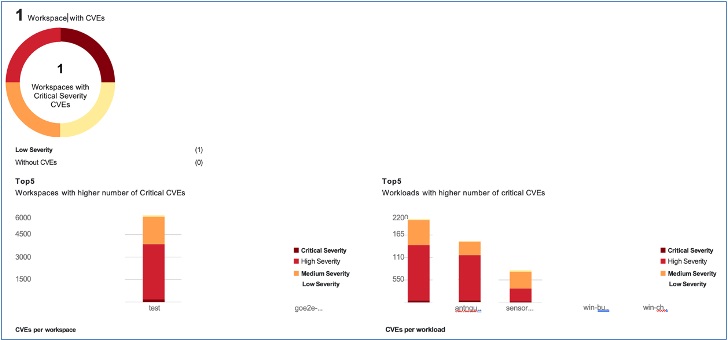
Workspaces with CVEs
Based on the scope that is selected and the scoring system (v2 or v3), the common vulnerabilities and exposures (CVE) count highlights the vulnerabilities (sorted by the scores) on workloads in the selected scopes. See the distribution of workspaces and the workloads with the highest number of critical CVEs.
Software packages on a workload could potentially be associated with known vulnerabilities (CVE). Common Vulnerability Scoring System (CVSS) is used for assessing the impact of a CVE. CVE can have CVSS v2 and CVSS v3 score. To compute the vulnerability score, consider CVSS v3 if it is available, else CVSS v2 is considered.
Vulnerability score for a workload is derived from scores of vulnerable software that is detected on that workload. The Workload Vulnerability Score is calculated based on the CVSS scores, the vendor data, and the security research team may adjust when the data is missing or inaccurate. Higher the severity of the most severe vulnerability, lower is the score.