Secure Connector Client Maintenance
This document describes best practices to maintain your Secure Connector client installation.
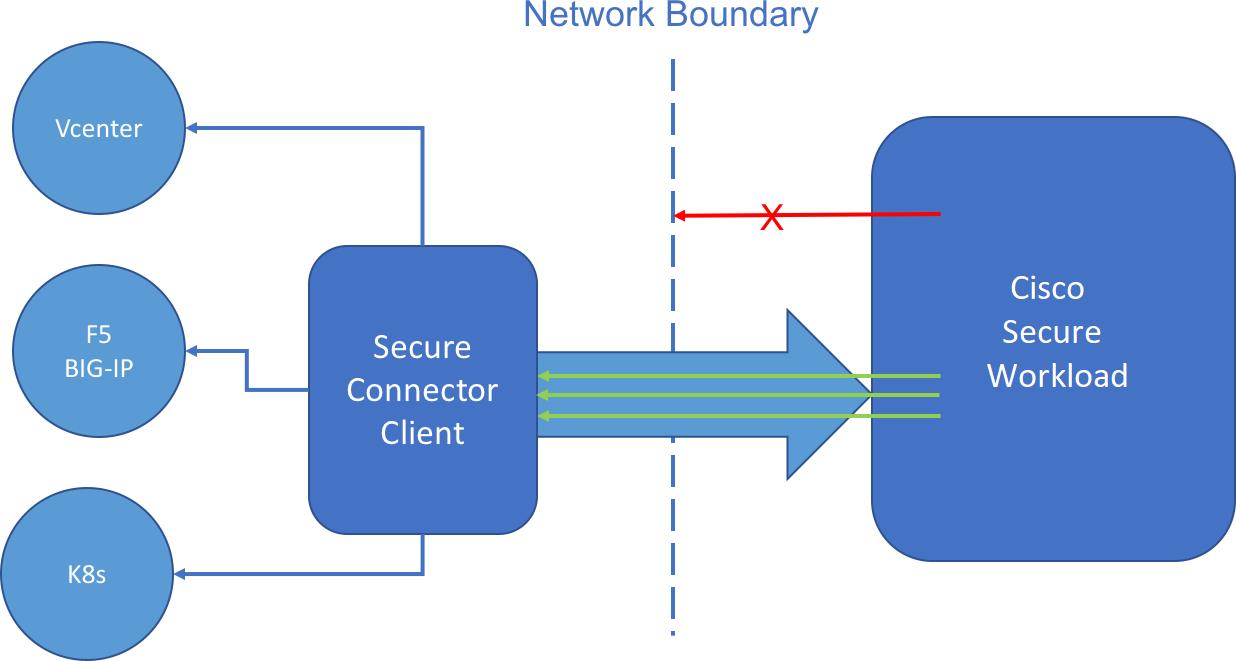
Secure Workload can be configured to import user tags or enforce policies on external orchestrators. For this, Secure Workload needs to establish outgoing connections to the orchestrator API servers (vCenter, Kubernetes, F5 BIG-IP, etc.).
Sometimes it is not possible for customers to allow direct incoming connections to the orchestrators from the Secure Workload cluster due to network boundaries such as cloud into Enterprise networks or from cloud to secure private endpoints in other clouds. In some cases, customers have partitioning within their enterprise networks that prevents connecting from Secure Workload clusters to other parts of the enterprise networks.
Secure Workload solves this issue by establishing an outgoing connection from the same network as the orchestrator to the Secure Workload cluster. This connection is used as a reverse tunnel to pass requests from the cluster back to the orchestrator API server.