Create Alerts
From the navigation pane, choose to configure the following alert types:
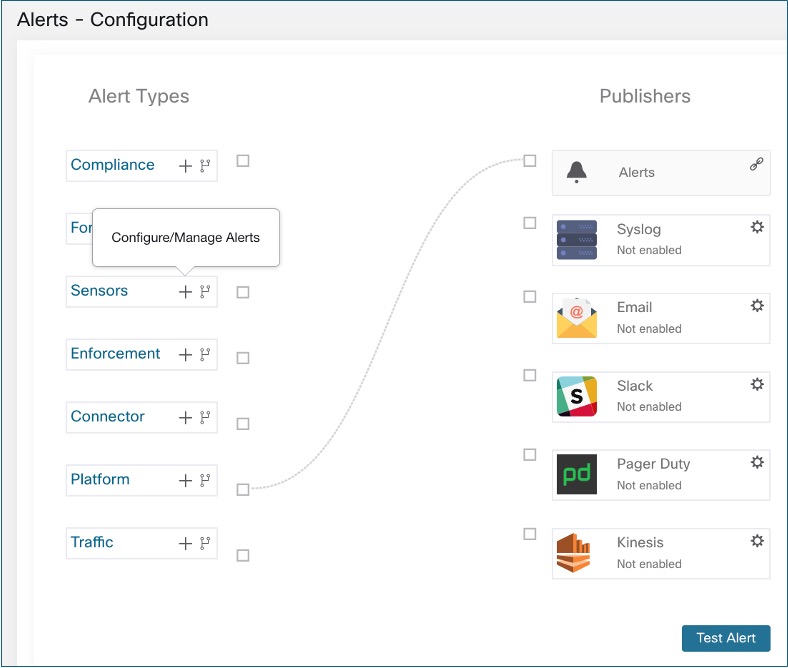
-
Enforcement Alerts
-
Agent Reachability
-
Workload Firewall
-
Workload Policy
-
-
Sensor Alerts
-
Agent Upgrade
-
Agent Flow Export
-
Agent Check In
-
Agent Memory Usage
-
Agent CPU Quota
-
Amount Of Flow Observations
-
New Agent Registered
-
Pcap Status
-
Agent Uninstalled
-
Not Recommended Cipher
-
Deprecated TLS Version
-
Agent Auto Removal
-
-
Compliance Alerts
-
Enforcement Policy
-
Live Analysis Policy
-
|
|
|
The following Alert Types do not have a configuration modal:
-
Forensics
-
Connectors
-
Traffic
Traffic Alerts
You can create Traffic alerts to notify you when workloads communicate with known malicious IPv4 addresses.
By default, the option to detect malicious addresses are disabled. To enable the option, see Visibility of Well-Known Malicious IPv4 Addresses section.
The available alert conditions are as follows:
-
Malicious flows are Observed: Indicates that communication with the known malicious IPv4 addresses has been observed.
-
Malicious flows are Permitted: After policy analysis and enforcement, this condition notifies you about malicious flows that have been permitted.
-
Malicious flows are Rejected: After policy analysis and enforcement, this condition notifies you about the malicious flows that have been rejected.
