Rule Attributes
This section explains the details of the attributes to define a Network Anomaly related rule. The simplest Network Anomaly rule is:
Event Type = Network Anomaly
Other attributes in the Network Anomaly event to refine the rules for your data centers:
|
Attribute |
Description |
|---|---|
|
Host Name |
The host name of the workload emitting this event. |
|
Timestamp (epoch milliseconds) |
The timestamp (in milliseconds) of the event. |
|
PCR Deviation |
The deviation of PCR from the mean at the event time as a multiple of historical standard deviation. |
|
Non-seasonal Deviation |
This is the PCR deviation after removing the seasonality pattern (for example, by cron-jobs). The value of Non-seasonal Deviation is always larger than or equal to 6.0. |
|
PCR |
The Producer-Consumer Ratio. |
|
EIR |
The Egress Ingress Ratio, which is the ratio between the total Egress App Byte Count and the Ingress App Byte Count. |
|
Egress App Byte Count |
The egress application byte count, which is the total byte count of packet contents (excluding headers) flowing out of the work-load. |
|
Ingress App Byte Count |
The ingress application byte count, which is the total byte count of packet contents (excluding headers) flowing into the work-load. |
|
Protocol |
The protocol for which the PCR time series is calculated. Currently, the supported protocols are TCP, UDP, and Aggregate. Aggregate PCR is calculated based on the total sum of TCP, UDP, and ICMP byte counts. |
|
User Logon Count |
The number of user login events on the workload within approximately the last 15 minutes. This is the count of the User Logon events regardless of whether there are matched rules. To know the details of the User Logon events, you must define rules to record the events for workloads of interests and view them on the Forensics Analysis page. |
|
User Logon Failed Count |
The number of users logon failed events on the workload within approximately the last 15 minutes. This is the count of the User Logon failed events regardless of whether there are matched rules. To know the details of the User Logon Failed events, you must define rules to record the events for workloads of interests and view them on the Forensics Analysis page. |
|
Unseen Command Count |
The number of unseen command events on the workload within approximately the last 15 minutes. This is the count of the Unseen Command events regardless of whether there are matched rules. To know the details of the Unseen Command events, you must define rules to record the events for workloads of interests and view them on the Forensics Analysis page. |
|
Date Time (UTC) - Year |
The year of the event time. |
|
Date Time (UTC) - Month |
The month of the event time (1, 2, . . . ). |
|
Date Time (UTC) - Day |
The day of a month of the event time (1, 2, . . . ). |
|
Date Time (UTC) - Hour |
The hour of a day of the event time (1, 2, . . . , 24). |
|
Date Time (UTC) - Minute |
The minute of an hour of the event time (1, 2, . . . , 60). |
|
Date Time (UTC) - Second |
The second of minute of the event time (1, 2, . . . , 60). |
|
Date Time (UTC) - Day of Week |
The day of a week of the event time (0-7, for Monday to Sunday). |
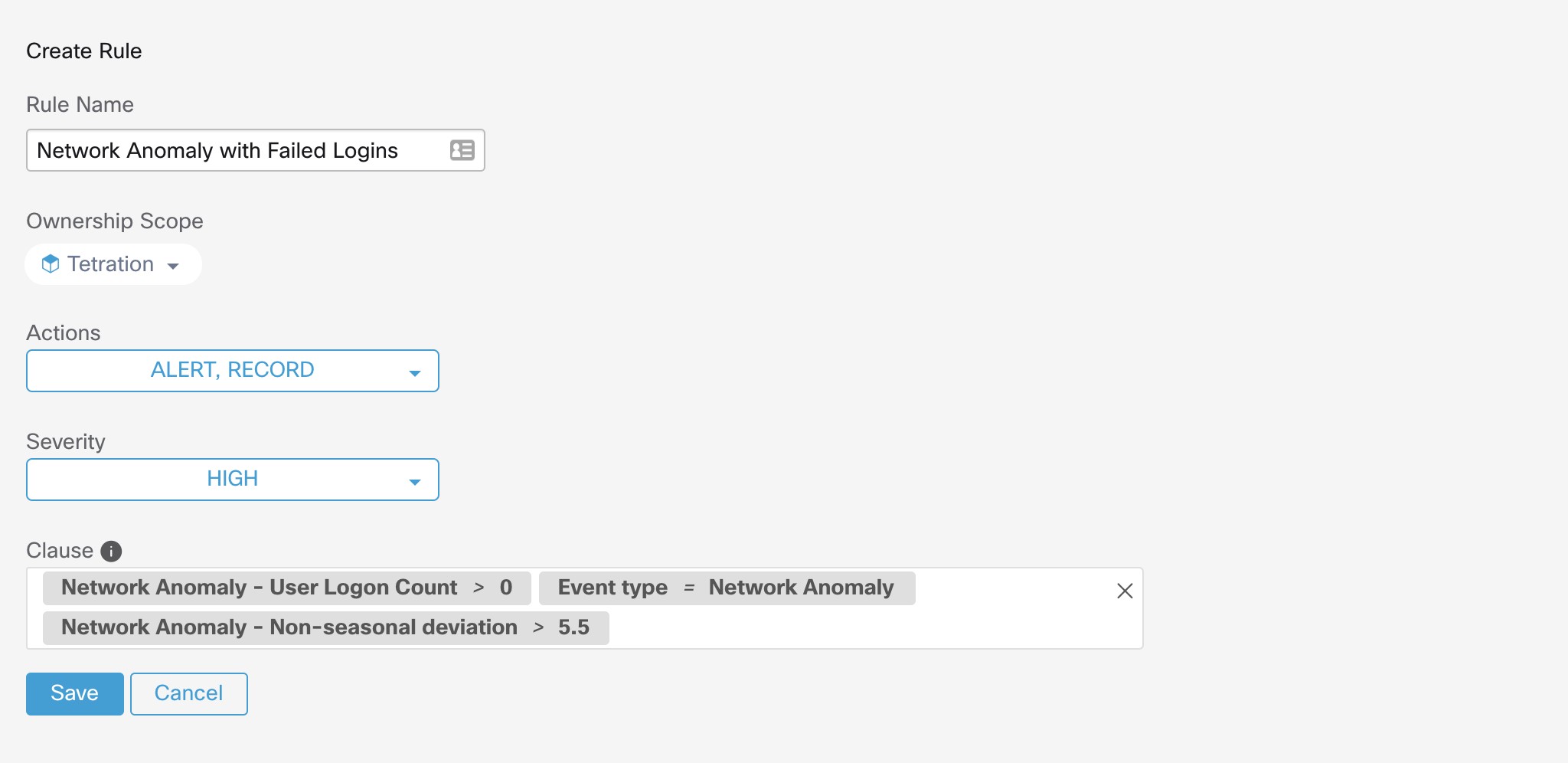
Below are some sample rules:
Listing 7.10.1.1.1: Detects network anomalies for UDP only.
Event Type = Network Anomaly AND Network Anomaly Is = Protocol - UDP
Listing 7.10.1.1.2: Detects large deviation after removing seasonal pattern (if detected), with a threshold on the egress app byte count for a subset of workloads whose names contain sensitiveDataServer.
Event Type = Network Anomaly AND Network Anomaly - Non-seasonal Deviation > 10.0)
AND Network Anomaly - Egress App Byte Count > 1000000
AND Network Anomaly - Host Name CONTAINS sensitiveDataServer
Listing 7.10.1.1.3: Detects Network Anomaly events on workloads with unseen command events except the Network Anomaly events happen from 7.30AM UTC to 7.35AM UTC everyday.
Event Type = Network Anomaly AND Network Anomaly - Unseen Command Count > 0
AND ( Network Anomaly - Date Time (UTC) - Hour != 7
OR Network Anomaly - Date Time (UTC) - Minute < 30 OR Network Anomaly - Date Time (UTC) - Minute > 35 )
