Policies Based on User Group or User Name
Use the following information to verify and troubleshoot policies based on user name (with and without user group name) on Windows OS workloads.
Sections in this topic describe the way that the policies should appear on the workload.
Examples in this topic are based on policies that are configured with the following information:
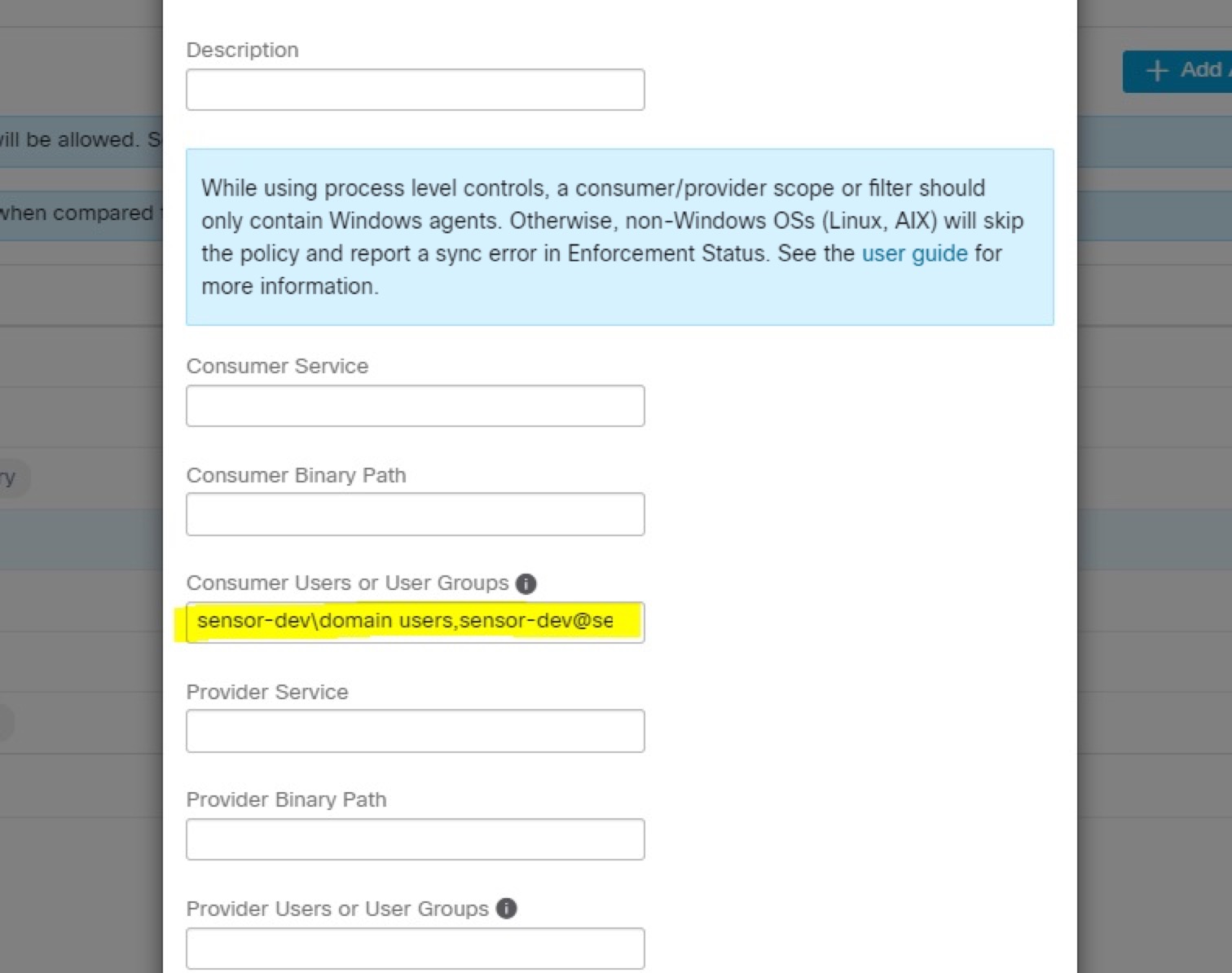
Sample Policy Based on User Name
dst_ports {
start_port: 30000
end_port: 30000
provider_filters {
user_name: “sensor-dev\sensor-dev”
}
}}
ip_protocol: TCP
address_family: IPv4
inspection_point: EGRESS
Sample Policy Based on User Group and User Name
dst_ports {
start_port: 30000
end_port: 30000
provider_filters {
user_name: “sensor-dev\domain users,sensor-dev\sensor-dev”
}
}}
ip_protocol: TCP
address_family: IPv4
inspection_point: EGRESS
Generated Firewall Rule
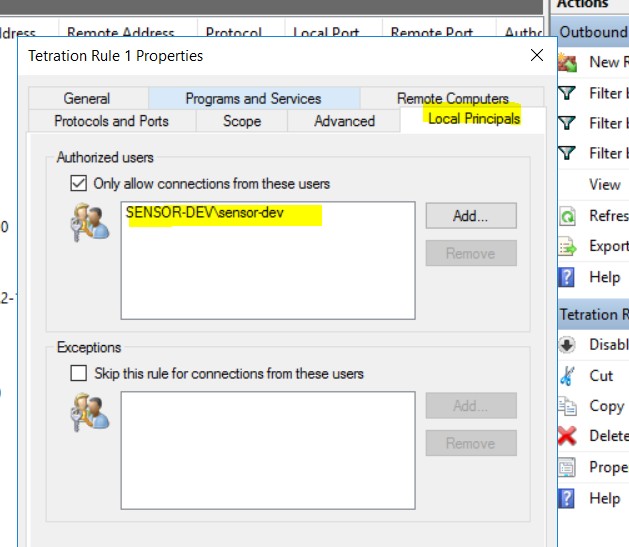
Firewall Rule Based on User Name
Example: Firewall rule based on User Name, sensor-dev\\sensor-dev
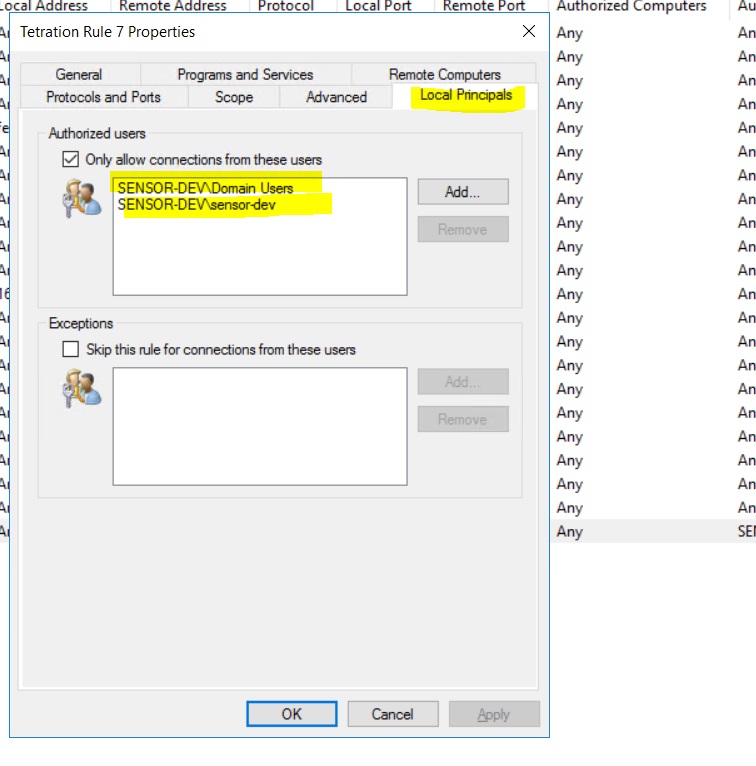
Firewall Rule Based on User Group and User Name
Example: Firewall rule based on User Name, sensor-dev\\sensor-dev and user group, domain users\\sensor-dev
Generated Filter Using netsh
To verify using native Windows tools that a filter has been added for an advanced policy:
-
With administrative privileges, run
cmd.exe. -
Run
netsh wfp show filters. -
The output file, filters.xml, is generated in the current directory.
-
Check FWPM_CONDITION_ALE_USER_ID for user name in the output file: filters.xml.
<item> <fieldKey>FWPM_CONDITION_ALE_USER_ID</fieldKey> <matchType>FWP_MATCH_EQUAL</matchType> <conditionValue> <type>FWP_SECURITY_DESCRIPTOR_TYPE</type> <sd>O:LSD:(A;;CC;;;S-1-5-21-4172447896-825920244-2358685150)</sd> </conditionValue> </item>
Generated WFP Filters Using tetenf.exe -l -f
Filter based on User Name
Example: WFP Rule based on User Name, SENSOR-DEV\sensor-dev
Filter Name: Secure Workload Rule 1
------------------------------------------------------
EffectiveWeight: 18446744073709551590
LayerKey: FWPM_LAYER_ALE_AUTH_CONNECT_V4
Action: Permit
RemoteIP: 10.195.210.15-10.195.210.15
Remote Port: 30000
Protocol: 6
User or Service: SENSOR-DEV\sensor-dev
Filter based on User Group and User Name
Example: WFP Rule based on User Name, SENSOR-DEV\\sensor-dev and User Group name, SENSOR-DEV\\Domain Users
Filter Name: Secure Workload Rule 1
------------------------------------------------------
EffectiveWeight: 18446744073709551590
LayerKey: FWPM_LAYER_ALE_AUTH_CONNECT_V4
Action: Permit
RemoteIP: 10.195.210.15-10.195.210.15
Remote Port: 30000
Protocol: 6
User or Service: SENSOR-DEV\Domain Users, SENSOR-DEV\sensor-dev
Service name and user name cannot be configured for a Network policy rule.
|
|
The network policy is rejected by the Windows agent if the user name or the user group is invalid. |
