Operation Summary for Workload, Telemetry and Segmentation
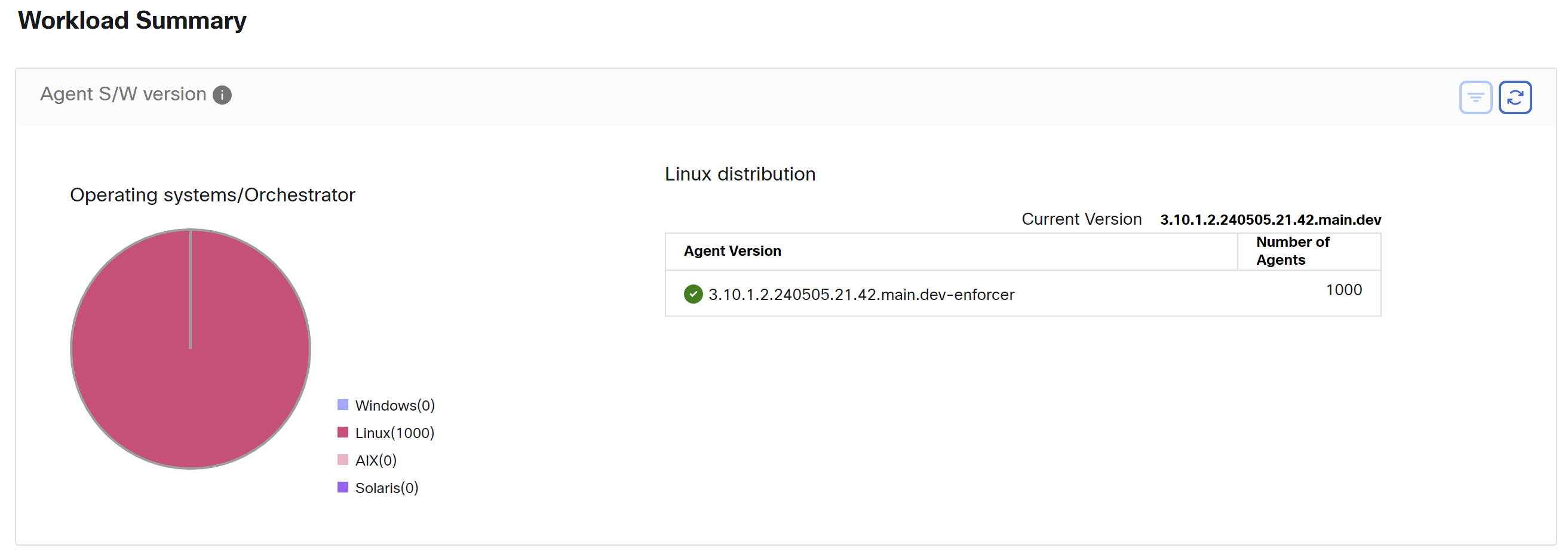
Workload Summary
Workload summary provides a view of the total agents that are deployed on one or more servers and endpoints in the network. The agents monitor and collect network flow information, enforce security policies with firewall rules on the installed hosts, communicate the status of the workload, and receive updates on the security policies.
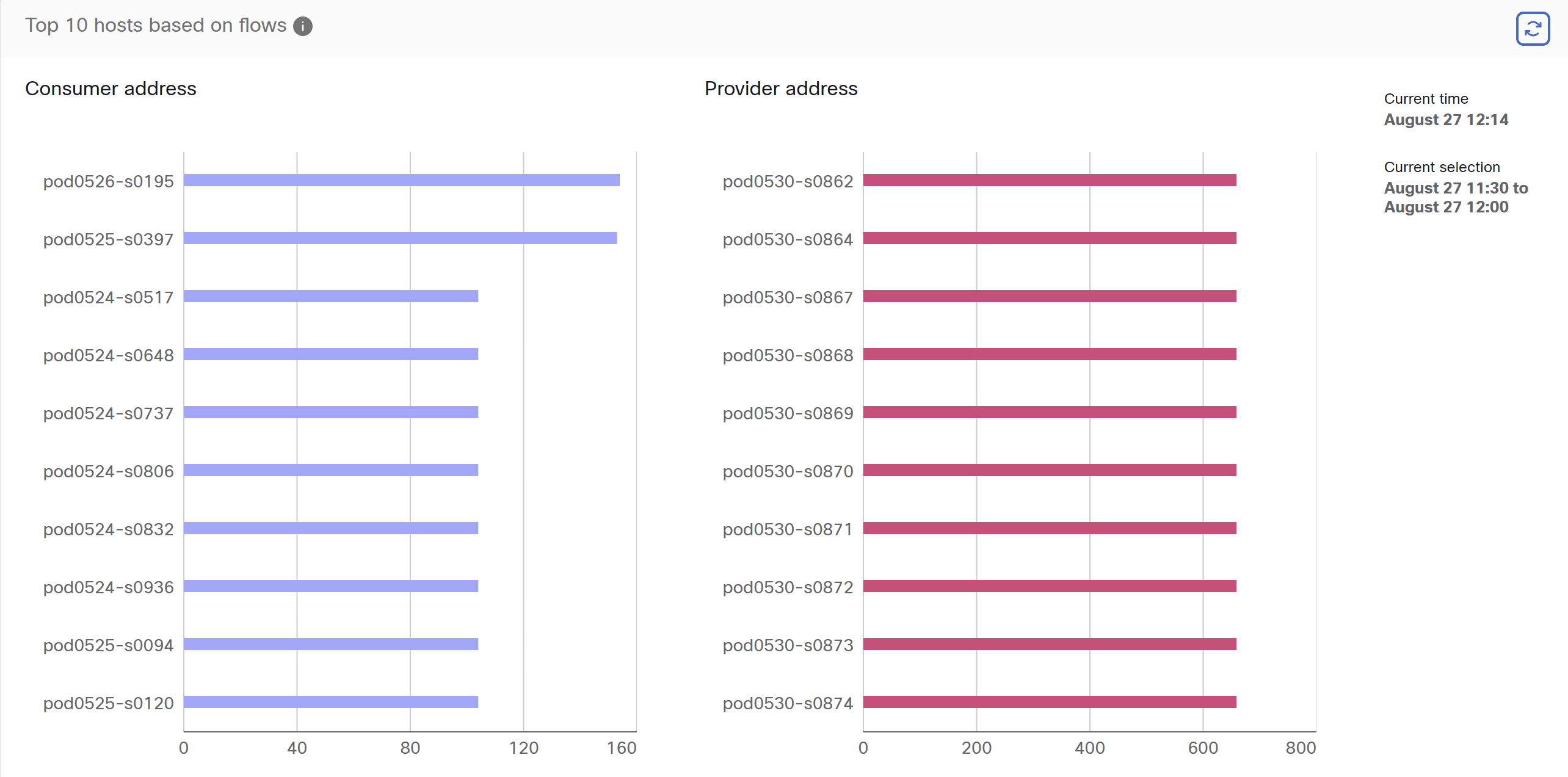
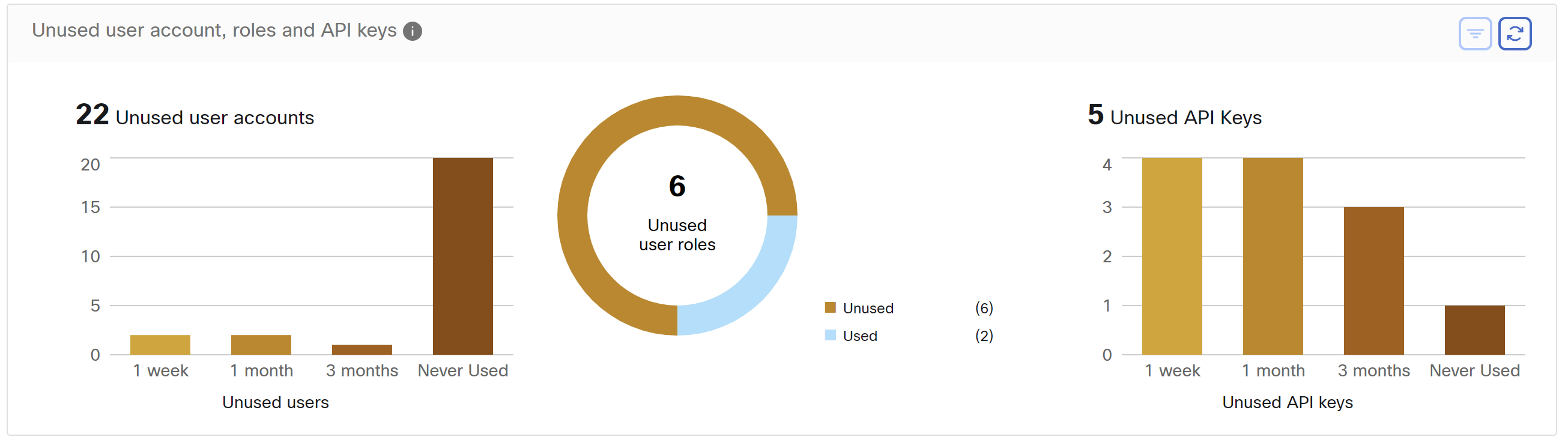
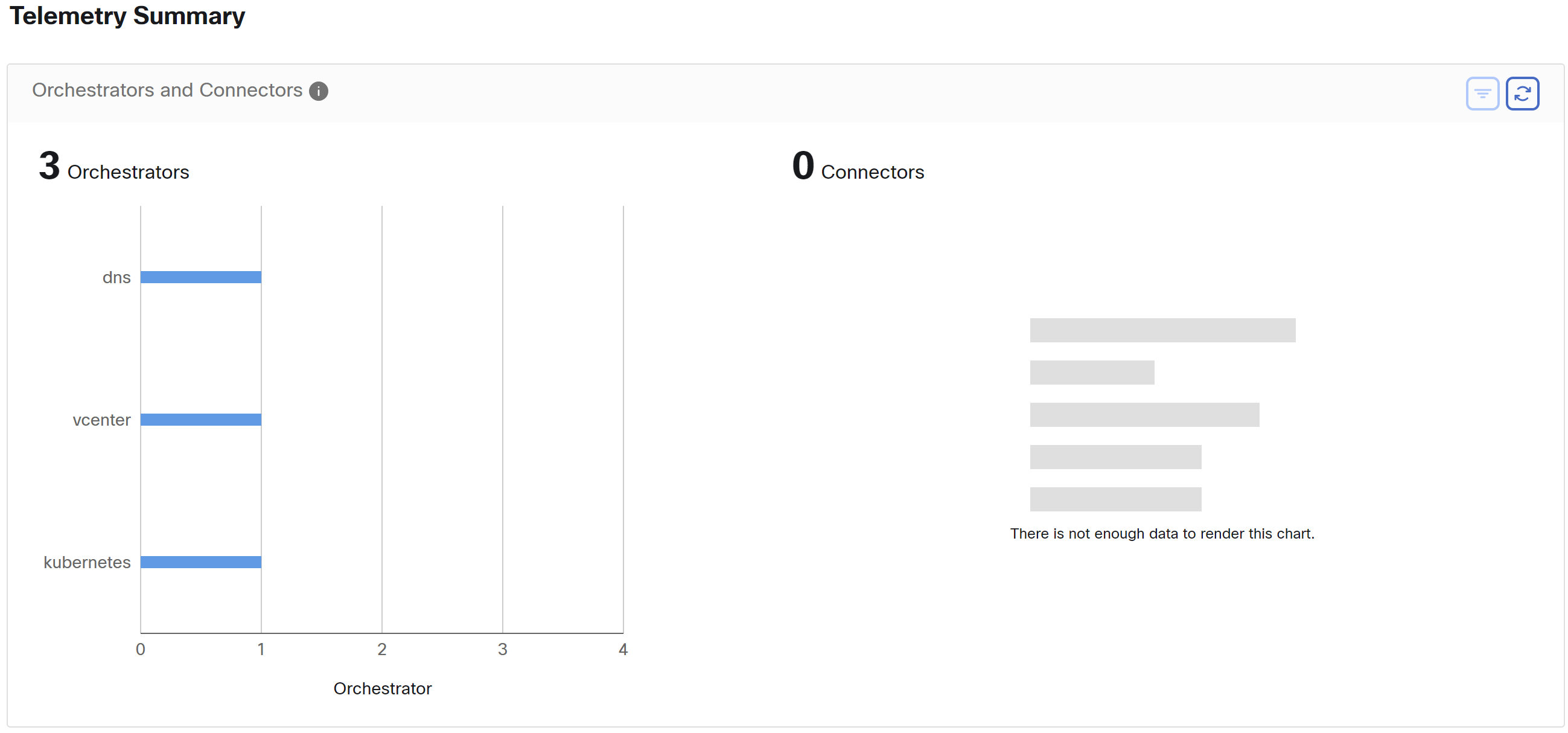
Telemetry Summary
Many connectors that are deployed on the virtual appliance collects telemetry from various points in the network, these connectors must listen on specific ports on the appliance. Connectors can ingest flow logs if you have setup flow logs for your specific security groups. You can also use the telemetry data for visualization and segmentation policy generation.
Cluster Summary
Site Admins can access the cluster status page, but the actions can be carried out only by Customer Support. It shows the status of all the physical servers on the Cisco Secure Workload rack.
The processing and retention time for clusters refer to the duration for which data is stored and processed within a cluster. The specific processing and retention times depend on the requirements of the workload and the policies of the organization.
It is important to consider the processing time requirements when configuring the cluster, as this can impact the storage capacity and processing power that is needed to meet the workload's needs.
Retention time refers to the length of time that data is retained within a cluster. For some workloads, data may need to be retained for regulatory or compliance purposes, while for others it may be deleted once it has been processed. It is important to establish retention policies for the workload to ensure that data is retained for the appropriate length of time and then deleted securely to prevent unauthorized access.
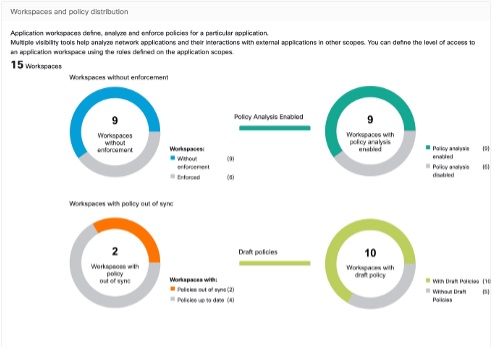
Segmentation Summary
Segmentation or Application Workspaces are the building blocks for discovering, applying, and managing policy and enforcement within the cluster. The segmentation summary captures the configuration details for each of the Application Workspaces implemented, the no. of workspaces with and without enforcement, policies that have been enabled or disabled, workspaces that have up-to-date policies or out of sync, and with or without draft policies.

