Roles
You can restrict access to features and data using role-based access control (RBAC) model.
-
User - someone with login access to Cisco Secure Workload.
-
Role - user created set of capabilities that is assigned to a user.
-
Capability - scope + ability pair
-
Ability - collections of actions
-
Action - low-level user action such as “change workspace name”
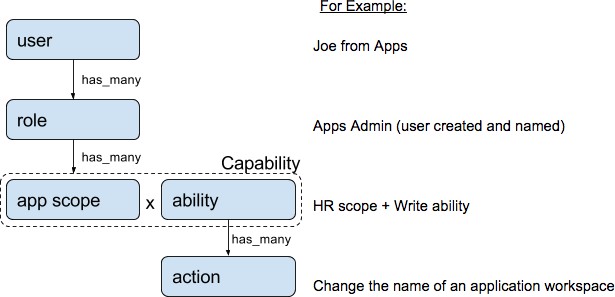
A user can have any number of roles. Roles can have any number of capabilities. For example, the “HR Search Engineer” role could have two capabilities: “Read on the HR Scope” to give visibility and context and “Execute on “HR:Search” capability to allow the engineers assigned this role to make specific changes that are related to their applications.
Use the Users page to assign users to the different roles. Roles have several capabilities and you can assign users to any number of roles.
System roles are defined to allow users to get started more quickly. They define different levels of access to all Scopes, that is, all data on the system. These system roles are defined below.
|
Role |
Description |
|---|---|
|
Agent Installer |
Provide the ability to manage agents life cycle including install, monitor, upgrade, and convert, but cannot delete agents and access agent config profile. |
|
|
If required, you can create a SecOps user role to provide the ability to access flows, alerts, vulnerabilities, and forensics events within a specific scope. |
