Process List Tab
This tab shows list of processes running on the host. A filter is also available to narrow down the list of processes based on the attributes of a process shown in table header below.
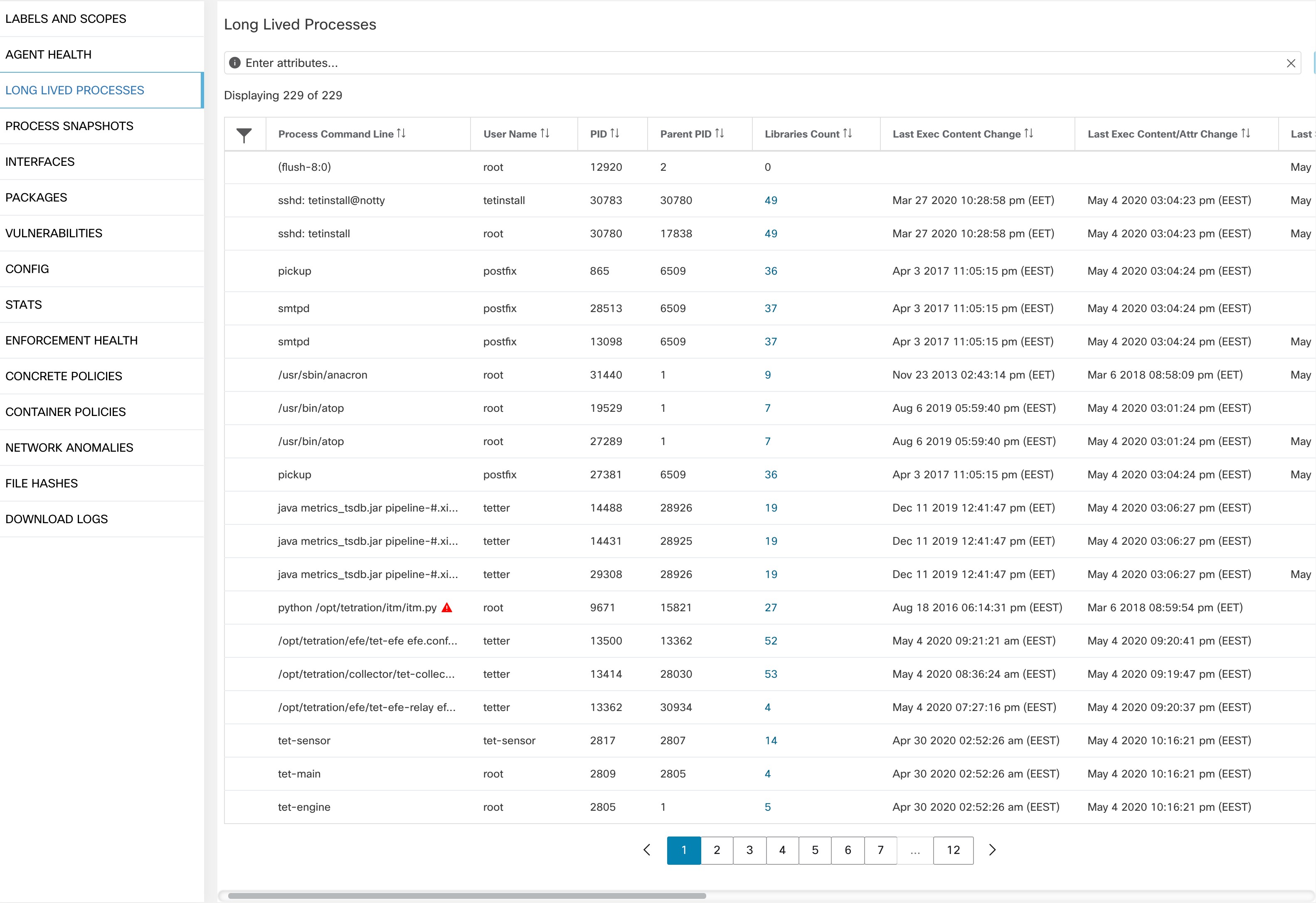
Attribute Descriptions:
|
Attribute |
Description |
|---|---|
|
Last Exec Content Change |
Similar to mtime in linux. It is the timestamp when only the file content changes. |
|
Last Exec Content Change |
Similar to ctime in linux. It is the timestamp when either the file content or attribute changes. |
|
Last Seen |
Last time when the process is observed. Available when the process is dead. |
|
CPU Usage |
CPU usage trend by the process in the past hour. |
|
Memory Usage |
Memory usage trend by the process in the past hour. |
|
Process Binary Hash |
SHA256 hash of the process binary in hex string, also known as process hash for short. Not available for kernel processes. |
|
Anomaly Score |
Process hash (anomaly) score. See Process hash anomaly detection for more information. |
|
Verdict |
Verdict of the process hash (either Malicious or Benign). The verdict is determined based on whether the process hash belongs to any user-defined hash list or known threat-intelligence hash database. See Process hash anomaly detection for more information. |
|
Verdict Source |
Source of the verdict. The verdict source can be either User Defined, or Secure Workload Cloud, or NIST. This attribute is known as Hash DB Source in previous releases. See Process hash anomaly detection for more information. |
