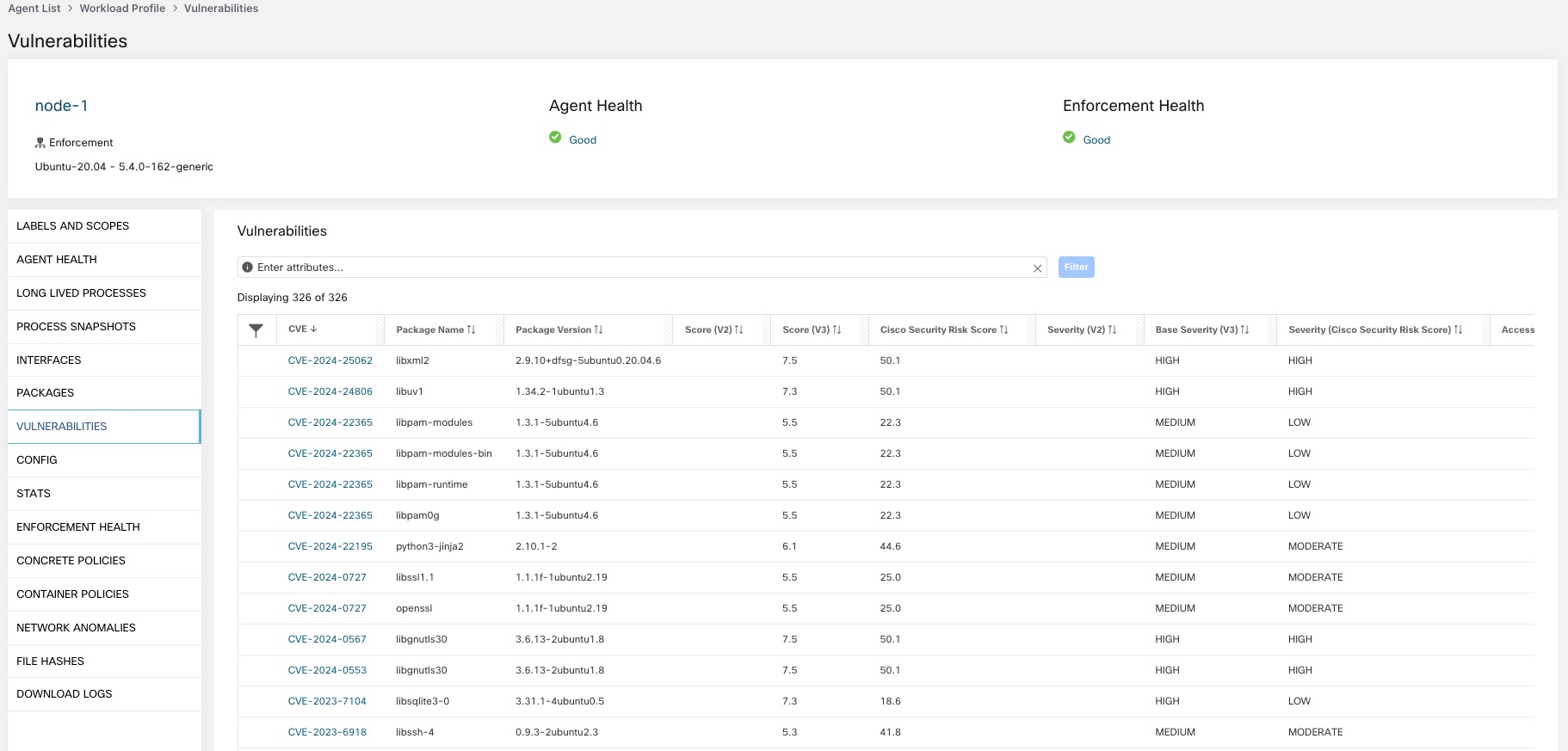
Vulnerabilities Tab
The VULNERABILITIES tab displays the CVEs identified by Secure Workload on the workload.
For each CVE, besides basic impact metrics, exploit information based on our threat intelligence is displayed:
-
Exploit Count: Number of times CVE was seen exploited in the wild in the last year
-
Last Exploited: Last time CVE was seen exploited in the wild by our threat intelligence