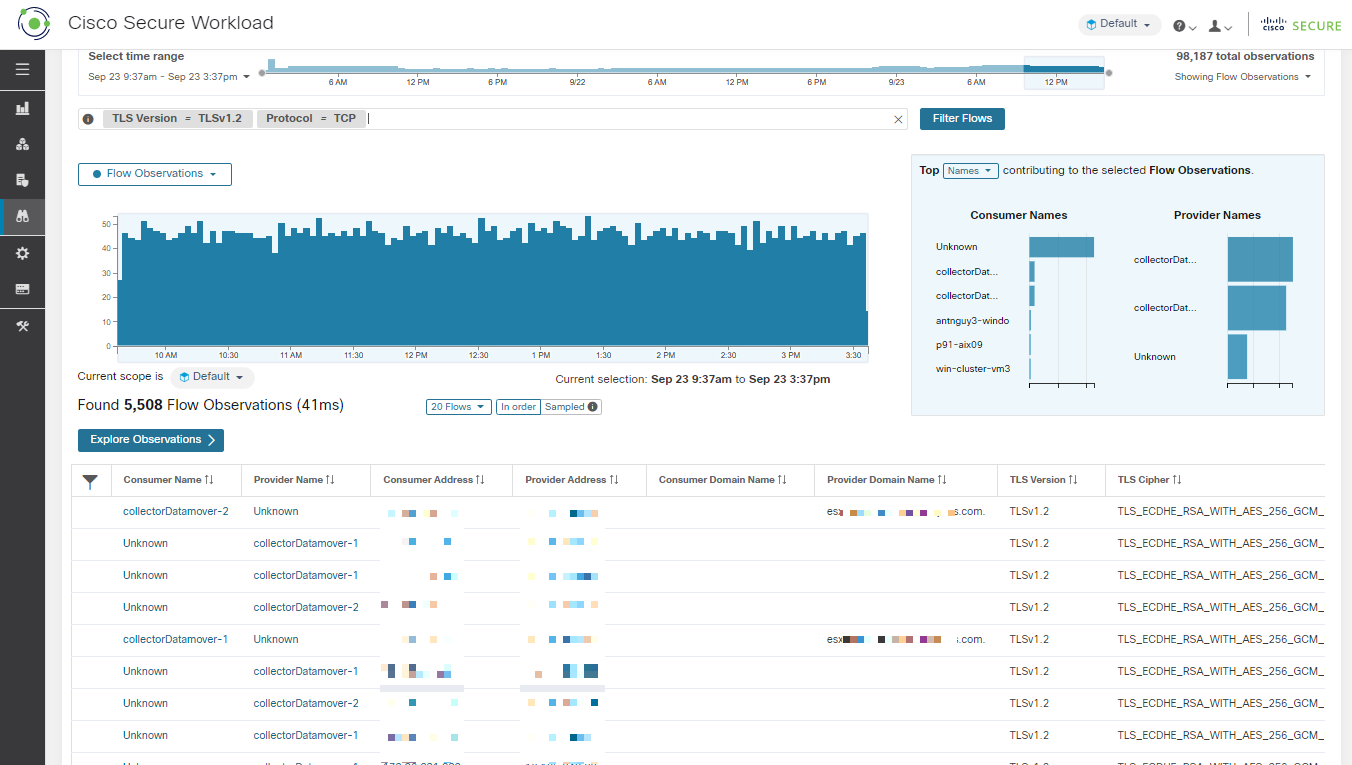
Network Traffic Flows
There are two sides of a traffic flow - Consumer and Provider. The consumer initiates the flow, and the provider responds to the consumer (for example Client and Server respectively).
Each observation tracks the number of packets, bytes, and other metrics in each direction for that flow for that minute interval. In addition to quickly filtering, the flows can be explored visually with Explore Observations. The resulting list of flows observations can be clicked to view details of that flow, including latency, packets, and bytes over the lifetime of that flow.
|
|
For hosts instrumented with Deep Visibility Agents or Enforcement Agents, Secure Workload is able to correlate flow data against the process that provides or consumes the flow. As a result, full command-line arguments, which may include sensitive information such as database or API credentials, used to launch the process are available for analysis and display. |