Data Model of Secure Workload Network Policy
Picture below shows a simplified UML diagram of Secure Workload entities exposed to Kafka:
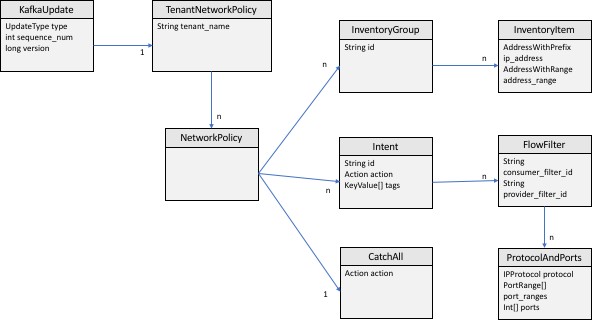
A Secure Workload Network Policy as modeled in protobuf consists of a list of InventoryGroups, a list of Intents and a CatchAll policy. Each policy contains all the items belonging to one root scope. An InventoryGroup contains a list of InventoryItems, which represent Secure Workload entities such as servers or appliances by specifying their network address, be it a singular network address, subnet or address range. An Intent describes action (allow or deny) to be taken when a network flow matches with the given consumer’s InventoryGroup, provider’s InventoryGroup and network protocols and ports. The CatchAll represents the catch-all action that is defined for the root scope inside Secure Workload. If no workspace with enforcement enabled exists for the root scope, a default policy of ALLOW is written to the produced policy.
When an enforcement is triggered by the users or by a change of inventory groups, Secure Workload backend sends a full snapshot of defined network policies to Kafka as a sequence of messages that are represented as KafkaUpdates. Refer to KafkaUpdate’s comments in tetration_network_policy.proto file for details how to reconstruct those messages to a full snapshot and how to handle error conditions.
In case KafkaUpdate message size is greater than 10MB, Secure Workload backend splits this message into multiple fragments, each of size 10MB. If there is multiple fragments, only the first fragment has the ScopeInfo field of TenantNetworkPolicy. The ScopeInfo will be set to nil in the remaining fragments of KafkaUpdate message.
