Policies
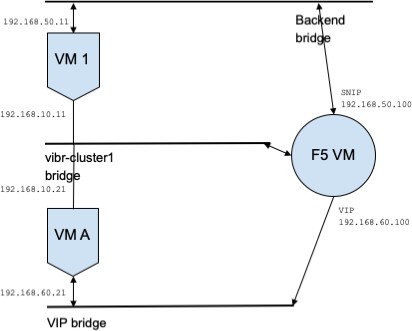
Assume we have a service db with VIP 192.168.60.100, SNIP 192.168.50.100, and a backend VM with IP 192.168.50.11 listening on port 10000. Traffic from client VM 192.168.60.21 to db results in the following policies:
-
Policy from client to VIP
The following policy permits from the client VM to service db.
{ "src": "<uuid of client scope>", "dst": "<uuid of service cluster>", "l4_params": [ { "port": [ 10000, 10000 ], "proto": 6, } ] } -
Policy from SNIP to BE.
A policy permitting traffic from the SNIP to the BE is autogenerated from configuration, and shows up as a related policy for db.
{ "src": "<uuid of SNIP cluster>", "dst": "<uuid of be scope>", "l4_params": [ { "port": [ 10000, 10000 ], "proto": 6, } ]A policy connector from the lb scope to the be scope pushes the following policy to it.
Consumer
Provider
Port
Protocol
Action
SNIP
be
10000
TCP
Allow
This generates firewall rules on BE host 192.168.50.11 allowing incoming traffic from LB SNIP 192.168.50.100 on port 10000.
-
Policy from HIP to BE.
A policy permitting traffic from the HIP to the BE is autogenerated from configuration, and shows up as a related policy for db.
{ "src": "<uuid of HIP cluster>", "dst": "<uuid of be scope>", "l4_params": [ { "port": [ 0, 0 ], "proto": ICMP, } ] }A policy connector from the lb scope to the be scope pushes the following policy to it.
Consumer
Provider
Port
Protocol
Action
HIP
be
0
ICMP
Allow
This generates firewall rules on BE host 192.168.50.11 allowing incoming ICMP traffic from LB HIP 192.168.50.2.
