Searching Inventory
Searching for inventory displays information about specific inventory items.
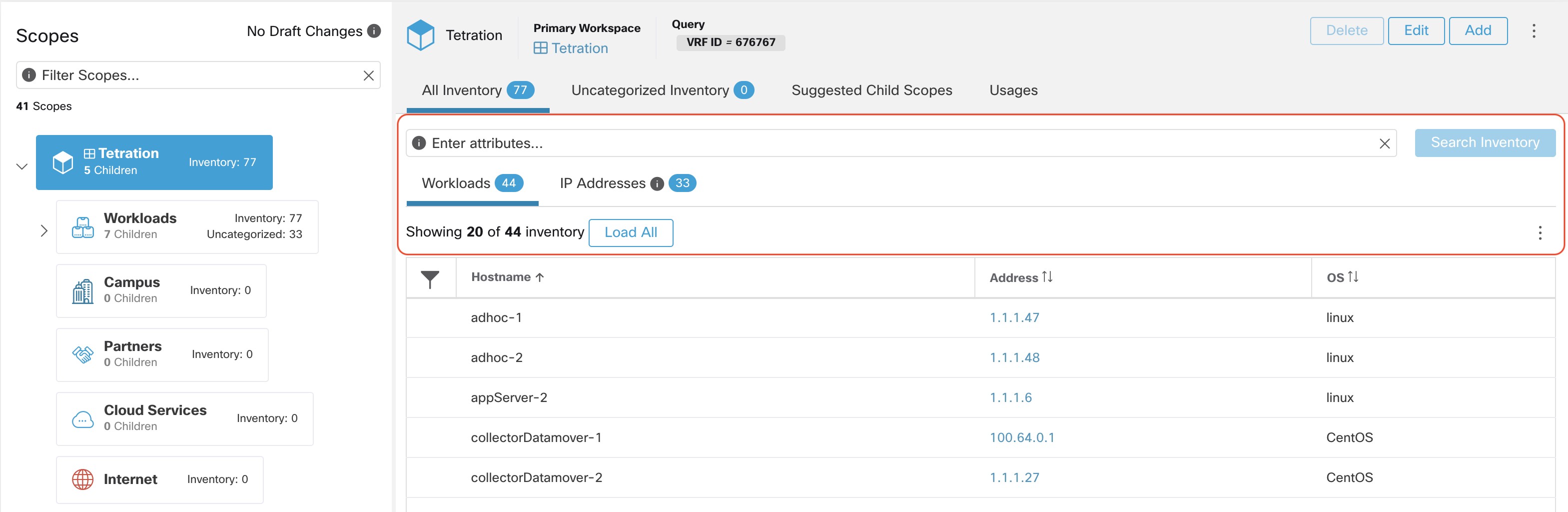
Procedure
| 1 |
From the navigation pane, choose . |
||||||||||||||||||||||||||||||||||||||||||||||||||||
| 2 |
Enter the attributes in the Filters field for the inventory items that you are looking for. The attributes include the following:
|
||||||||||||||||||||||||||||||||||||||||||||||||||||
| 3 |
Click Search Inventory. The results are displayed below the Filters field that is grouped into four tabs. Each tab displays a table with the relevant columns. Additional columns can be displayed by clicking on the funnel icon in the table header. If any user labels are available, they will be prefixed with and can be toggled here. 

The search results are grouped into four tabs:
There is also a mention of the inventory count next to each tab. The immediately available information in a search includes hostname, IP Addresses with subnets, OS, OS Version, Service Name and Pod Name. The list of displayed columns can be toggled by clicking the funnel icon in the table header. Search results are restricted to the currently selected scope shown in the scope directory. More information can be seen on the respective profile page by clicking on an item in the search results. More details about each host is displayed on the Workload Profile, which is accessible by clicking on the IP address field of a search result row. See the Workload Profile for more information. To create Inventory Filters via the sidebar: Choose from the top-level menu. Click the Create Filter button. A modal dialog appears where you can name your saved filter. |
