Summary Reports of Segmentation, Workload, Traffic Flow and Security
The overview section provides real-time insights into the network flow information, security policies, system performances, and security threats. It enables security analysts and network administrators to make informed decisions and take measures to protect their data resources.
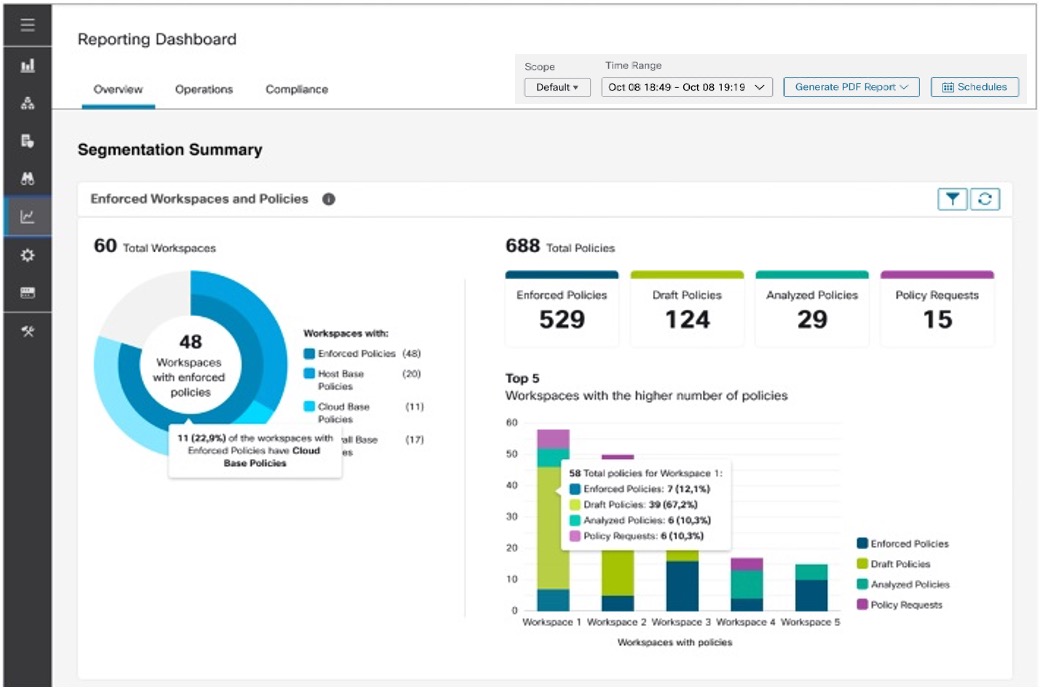
Segmentation Summary
Workspaces are the building blocks to discover, apply, and manage policies and enforcement within the cluster. You can define segmentation memberships by selecting the appropriate scope.
Segmentation summary captures the configuration details for every workspace, all policy-related activities, such as defining, analyzing, and enforcing policies for a particular scope in the workspace or workspaces that are associated with that scope.
The graph displays a summary of the various policies that are associated with the workspaces.
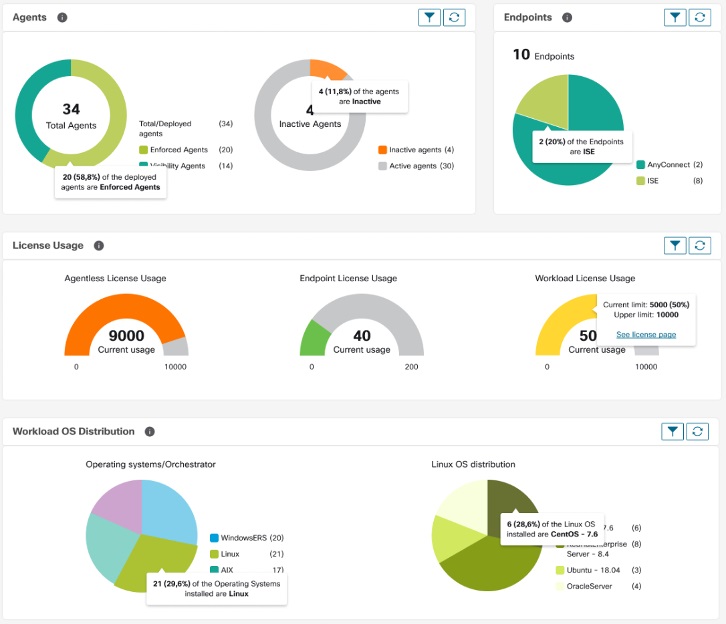
Workload Summary
The Workload summary provides the following details about the agents that are deployed on one or more servers and endpoints in the infrastructure:
-
Agents monitor and collect network flow information.
-
Agents enforce security policies with firewall rules on the installed hosts.
-
Agents communicate the status of the workload.
-
Agents receive updates on the security policies.
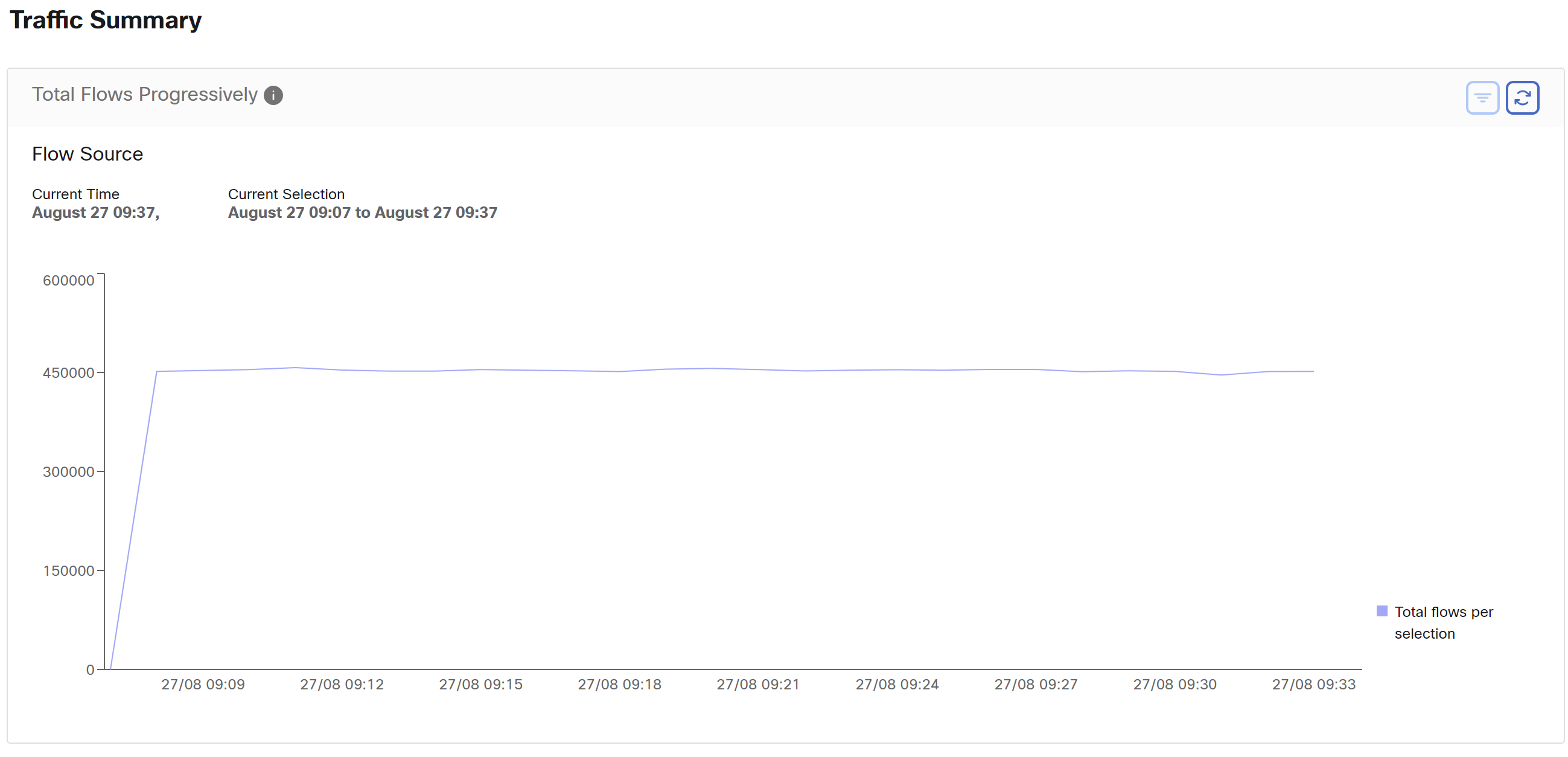
Traffic Summary
Traffic summary captures the flow observations of each flow. Each observation in the flow source tracks the number of packets, bytes, and other metrics for the flows.
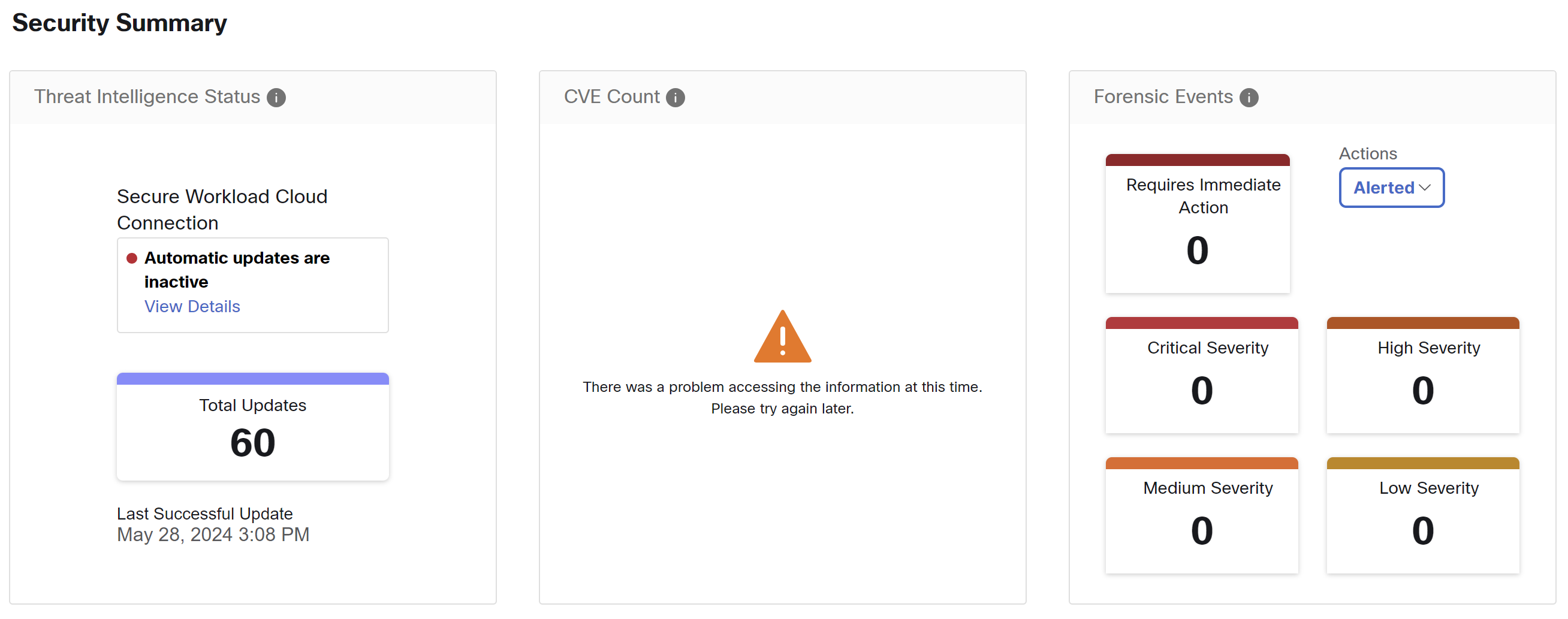
Security Summary
Security Summary provides Threat Intelligence Status (last time when the threat intelligence status updates were received are shown), count of CVEs, and distribution of Forensic events.