List of External Orchestrators
The External Orchestrators page shows the existing external orchestrators and provides functions to modify and delete them as well as to create new external orchestrators:
|
Type |
Description/ When to use |
|---|---|
|
VMware vCenter |
To import virtual machine data, such as host name, IP address, and labels, from a vCenter server to Secure Workload. The generated labels can be used to create Secure Workload scopes and enforcement policies. |
|
Amazon Web Services |
(You cannot create new AWS orchestrators; instead, create AWS connectors. See AWS Connector. Any existing AWS orchestrators are read-only). To import data of EC2 server instances, such as host name, IP address, and labels, from the given AWS account to Secure Workload. The generated labels are useful to create Secure Workload scopes and policies. |
|
Kubernetes/OpenShift |
To import Kubernetes’ entities, such as nodes, pods, services, and labels. These labels can be used within Secure Workload to define scopes and policies. |
|
DNS |
To import A/AAAA and CNAME records from a DNS server via zone transfer. This produces DNS names as labels, which are useful in defining Secure Workload scopes and policies. |
|
Infoblox |
To import networks, hosts, and A/AAAA records with extensible attributes from an Infoblox appliance with IPAM/DNS enabled. The imported extensible attributes can be used as labels in Secure Workload scopes and policies. |
|
F5 BIG-IP |
To read virtual server configurations from the given F5 load balancer and generate labels for the provided services, which can be used to define enforcement policies in Secure Workload. The policy enforcement feature will translate them into F5 policy rules via F5 REST API. |
|
Citrix Netscaler |
To read virtual server configurations from the given Netscaler load balancer and generate labels for the provided services, which can be used to define enforcement policies in Secure Workload. The policy enforcement feature will translate them into Netscaler ACLs via its REST API. |
|
Secure Firewall Management Center |
To deploy policies to all Secure Firewall Threat Defense (formerly known as Firepower Threat Defense or FTD) devices registered to the given Secure Firewall Management Center using REST API. |
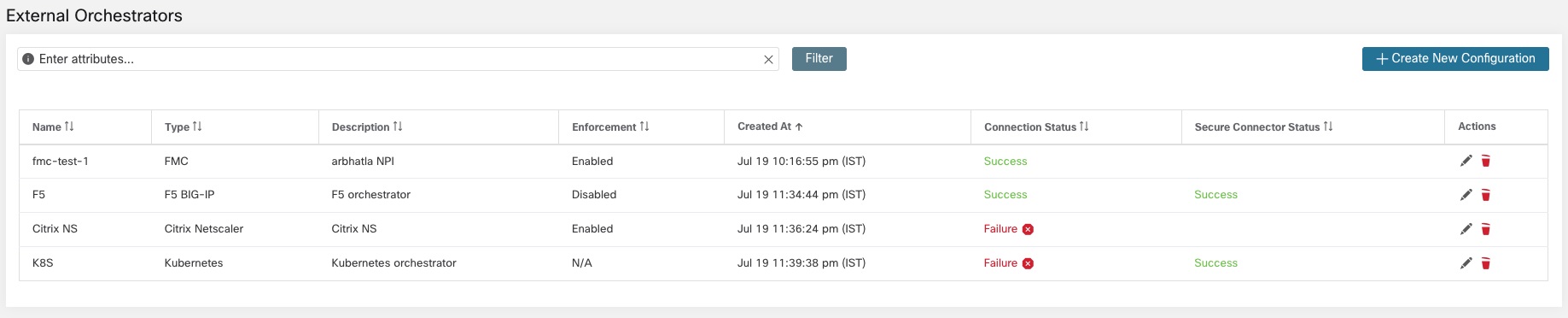
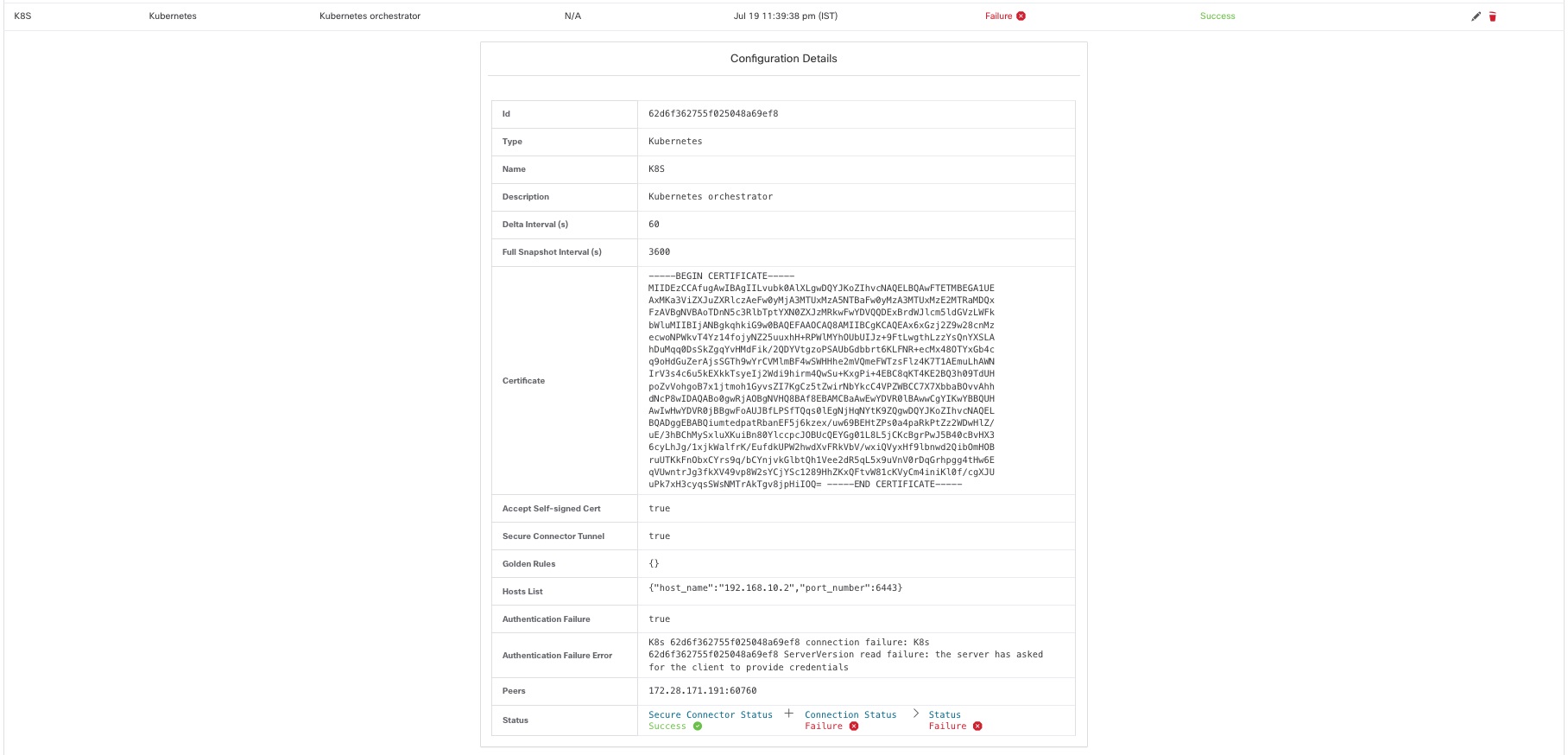
Each row shows a short version of the external orchestrator with its Name, Type, Description, Enforcement, Created at, Connection Status, and Secure Connector Status. The Connection Status tells if a connection to the given external data source could be made successfully. The Secure Connector Status displays the status of the Secure Connector tunnel- Success or Failure. If the tunnel is not enabled then N/A is displayed.
Enable Secure Connector tunnel while creating an external orchestrator configuration. If Secure Connector tunnel is enabled, the external orchestrator 'Connection Status' is dependent on both the authentication status and secure connector status. If Secure Connector tunnel is not enabled, the external orchestrator 'Connection Status' is only dependent on the authentication status. Irrespective of the status- Success or Failure, you can click the respective row to get more details. For more details on the Secure Connector client metrics, click the Status row or in the left pane, navigate to .