ISE Instance Configuration
|
|
Starting Cisco Secure Workload version 3.7, the SSL certificate for Cisco ISE pxGrid node requires Subject Alternative Names (SAN) for this integration. Ensure the certification configuration of the ISE nodes is done by your ISE administrator prior to performing the integration with Secure Workload. |
To verify your pxGrid node’s certificate and confirm if SAN is configured, you need to do the following to verify the certificate from ISE.
Procedure
| 1 |
Go to Certificates under . |
||||||||||||||||||||||
| 2 |
Under Certificate Management, select System Certificates, select your “Used by” pxGrid certificate and choose View to review the pxGrid node cert. |
||||||||||||||||||||||
| 3 |
Scroll the certificate and ensure the Subject Alternative Names are configured for this certificate. |
||||||||||||||||||||||
| 4 |
This certificate should be signed by a valid Certificate Authority (CA), which should also be used to sign the pxGrid client certificate used for the Secure Workload ISE connector. 
|
||||||||||||||||||||||
| 5 |
You can now generate the pxGrid client certificate signing request using the following template on any host installed with OpenSSL.
Save the file as ‘example-connector.cfg’ and use the OpenSSL command from your host to generate a Certificate Signing Request (CSR) and the certificate private key with the following command.
|
||||||||||||||||||||||
| 6 |
Sign the Certificate Signing Request (CSR) by your CA using a Windows CA server. If you are also using a Windows CA server, run the following command to sign the pxGrid client’s CSR.

|
||||||||||||||||||||||
| 7 |
Copy the signed client certificate and the root CA in PEM format onto your host. This is the same host that generates the client CSR and the private key. Use OpenSSL to ensure the client certificate is in X.509 PEM format. Run the following command using OpenSSL to convert the signed client certificate to the X.509 PEM format.
|
||||||||||||||||||||||
| 8 |
You can also confirm the PEM that is signed by the CA, use the following command.
|
||||||||||||||||||||||
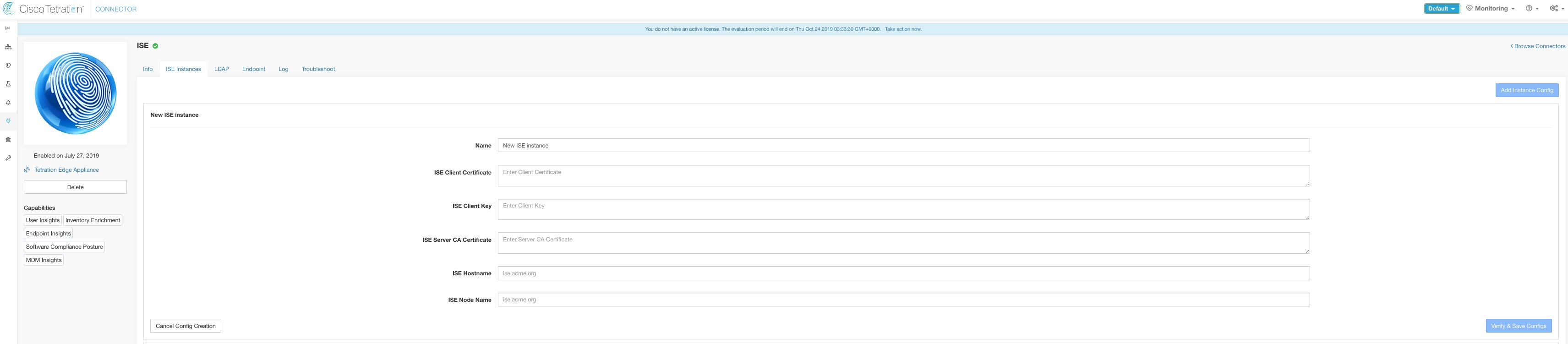
| 9 |
Using the above example’s file names, copy the ISE client cert - example-connector.pem, client key - example-connector.key and CA – root-ca.example.com.pem into the respective fields on the ISE configuration page on Secure Workload as shown below.


|
|
|
|
