End-to-End Migration Workflow
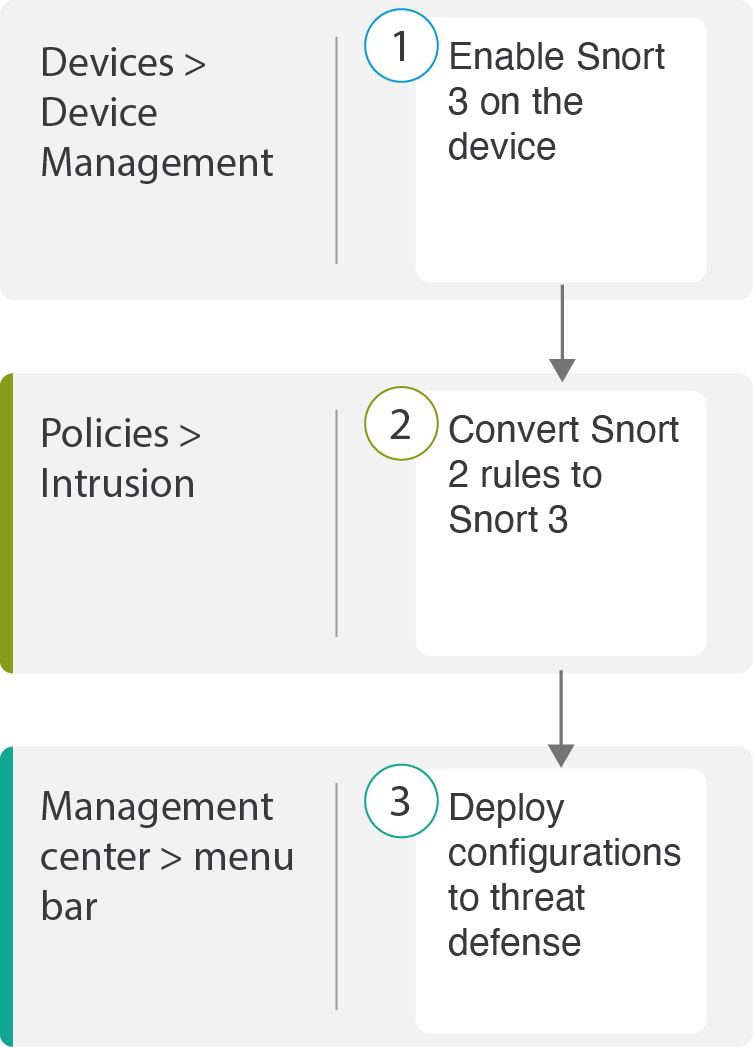
The following flowchart illustrates the workflow for migrating Snort 2 to Snort 3 in Secure Firewall Management Center.
|
Step |
Description |
|---|---|

|
Enable Snort 3 on the device. See Enable Snort 3 on Threat Defense. |

|
Convert Snort 2 rules to Snort 3. See Convert Snort 2 Rules of a Single Intrusion Policy to Snort 3. |

|
Deploy configuration. See Deploy Configuration Changes. |
